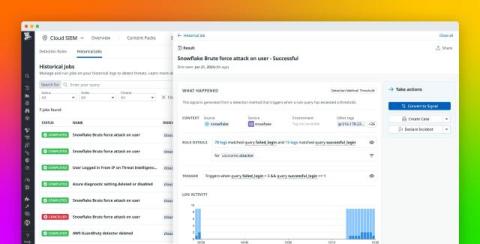
Backtest detection rules with Datadog Cloud SIEM Historical Jobs
Every security engineer has experienced this issue: after spending a lot of time creating a new SIEM alert to catch malicious behavior, you deploy it, only to find there are over 100 service accounts triggering false positives. Your SIEM is suddenly flooded with false alerts, and your team is overwhelmed as a result. You then spend hours or even days investigating these alerts and fixing your detection rule, hoping it will work better next time.