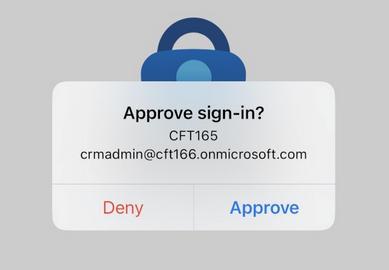
Kroll insights hub highlights key AI security risks
From chatbots like ChatGPT to the large language models (LLMs) that power them, managing and mitigating potential AI vulnerabilities is an increasingly important aspect of effective cybersecurity. Kroll’s new AI insights hub explores some of the key AI security challenges informed by our expertise in helping businesses of all sizes, in a wide range of sectors. Some of the topics covered on the Kroll AI insights hub are outlined below.