Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
The Dirty Pipe vulnerability: Overview, detection, and remediation
The situation with Dirty Pipe is rapidly evolving. We will update the information in this blog as it is released publicly. On March 7, 2022, Max Kellermann publicly disclosed a vulnerability in the Linux kernel, later named Dirty Pipe, which allows underprivileged processes to write to arbitrary readable files, leading to privilege escalation. This vulnerability affects kernel versions starting from 5.8.
Hackers Breached Samsung, Stole Galaxy Source Code
Read also: Rompetrol hit by Hive ransomware, Mozilla fixes Firefox zero-days, and more.
Cyber Readiness and the Russia-Ukraine War
I was encouraged when I saw our partners over at Microsoft step in when Russian cyberattacks commenced alongside their invasion of the Ukraine. While there have yet to be any reported attacks on the United States or its allies, I can’t help but think about our collective readiness, especially as sanctions against Russia intensify. The Cybersecurity and Infrastructure Security Agency (CISA), a federal agency under the U.S.
How To Address SAST False Positives In Application Security Testing
Static Application Security Testing (SAST) is an effective and well-established application security testing technology. It allows developers to create high-quality and secure software that is resistant to the kinds of attacks that have grown more prevalent in recent years. However, the challenge with SAST is that it tends to produce a high number of false positives that waste the time of your engineering team. In this blog we take a look at SAST and the problem of false positives.
Cybersecurity Trends for 2022: Why Staying Ahead of the Threat Has Never Been So Critical
2021 was a devastating year for cybersecurity. As business accelerated digital adoption and people played out their lives online, threat actors were ready to capitalize on the transitional moment, savagely targeting everything from critical health infrastructure to small and medium-sized businesses. By Q4 of 2021, the number of reported data breaches had already surpassed 2020 totals, which were historic in their own right.
Top 7 Security Measures That Payment Gateways Use
Handling sensitive data, compliance, and security is always front of mind for payment gateways. Technology is nowadays a double-edged sword. Just as digital advancement has revolutionized global commerce, so too have the tactics that cybercriminals use to defraud merchants and customers. A study by PWC, Global Economic Crime and Fraud Survey 2020, found that 47% of respondent companies experienced some form of fraud, resulting in US$42B of losses.
AWS Penetration Testing | All You Need to Know
Amazon Web Services or AWS services has over a million users in around 190 countries and is an ever-growing and widely adopted platform as more and more companies tend to move toward a cloud environment.
Strengthening our investment in customer security with a $1 million bug bounty
At 1Password, we’re committed to providing an industry-leading security platform for both businesses and families. That’s why today, we’re announcing that we’ve increased our top bug bounty reward with Bugcrowd to $1 million. With this investment, we’re further bolstering our ongoing efforts to keep 1Password customers as secure as possible.
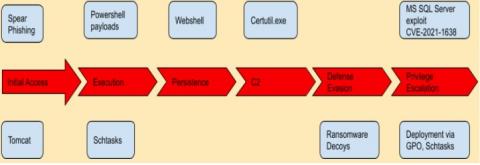
Detecting HermeticWiper
As stated in our previous threat advisory STRT-TA02 in regards to destructive software, past historical data suggests that for malicious actors to succeed in long-standing campaigns they must improve and add new ways of making their payloads stealthier, resistant, and damaging. HermeticWiper introduces some unique features, applying destructive actions on compromised hosts.