Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Ivan Tsarynny and Vitaliy Lim on Feroot's $11 Million Seed Funding to Improve Client-Side Security
Brilliant business ideas are driven by brilliant entrepreneurs. Enter Feroot’s own Ivan Tsarynny, CEO and Vitaly Lim, CTO, whose vision to improve client-side or “front-end” security for businesses around the globe resulted in the closing of $11 million in seed funding led by True Ventures. Feroot will use the funds to meet growing demand for client-side security solutions by accelerating product development and go-to-market initiatives.
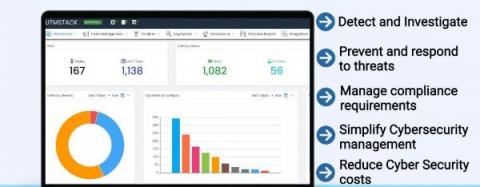
The Importance of Log Management and Cybersecurity
Struggling with the evolving cybersecurity threat landscape often means feeling one step behind cybercriminals. Interconnected cloud ecosystems expand your digital footprint, increasing the attack surface. More users, data, and devices connected to your networks mean more monitoring for cyber attacks. Detecting suspicious activity before or during the forensic investigation is how centralized log management supports cybersecurity.
Internet Security 101 - Free Security Suites and their reliability
With our mundane lives becoming more and more integrated with technology daily, it is important to impart awareness of the subject matter, as well. Technology and mainly the internet has changed the landscape of even our imagination, to say the least, and while it is still embarked on curving the bits and nooks of the world, some tweaks need to be paid attention to, also.
Healthcare Providers Need to Increase Budgets for Cybersecurity
The past few years have emphasized just how important cybersecurity is. As cybercrime reached record heights and more companies went digital, industries realized their current security efforts fell short. Healthcare is a prime example. The medical sector has had the second highest number of data breaches of any industry for more than five years. This became increasingly noticeable in 2019 alone, when the industry experienced 525 data breaches, up from 369 the year before.
SIEM as a Service
SIEM-as-a-Service (SaaS) and Managed SIEM services have gained popularity among companies aiming to meet security compliance standards in a cost-effective manner. Let’s see why a SIEM service can transform your small or mid-sized business’s cybersecurity.
Five worthy reads: New names, similar games-The evolution of phishing
Illustration by Derrick Deepak Roy Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore phishing attacks and how they’ve evolved in recent times. Way back in the 1990s, or so the story goes, users unwilling to pay for access to the internet would hunt for others’ login credentials to keep browsing for free.
Weekly Cyber Security News 11/03/2022
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. It has been a while since a really bad widespread issue with Linux hit, but here we are…
Empower Your SOC with New Applications in the CrowdStrike Store
With chaos seemingly surrounding us in security, it can be hard to cut through the noise. How do you detect and prioritize evolving threats and what tools should you use to address them? With new attacks and vulnerabilities on the rise, combined with ineffective security tools and the industry’s ongoing skill shortage, security operations center (SOC) teams struggle to protect organizations from adversaries.
Talking to your kids about online safety
Raising a family today means, for many parents, having kids who use the internet for entertainment, talking with friends, and schoolwork. Millions now have a smartphone around the time they lose their first tooth. This creates new challenges for parents who want to help their children navigate around mature content, misinformation, and other online risks.