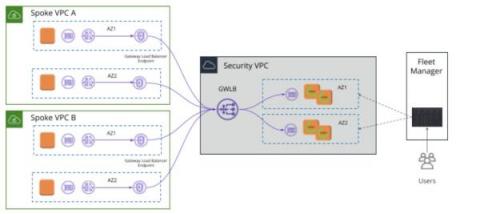
Monitoring AWS networks at scale
Corelight is pleased to announce our integration with AWS’s Traffic Mirroring to Gateway Load Balancer (GWLB) Endpoint as a Target. This integration simplifies the monitoring of network traffic and generating Corelight data in massively scaled-out public cloud environments. When it comes to monitoring network traffic today, we see two primary deployment patterns, each with their own pain points.