Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
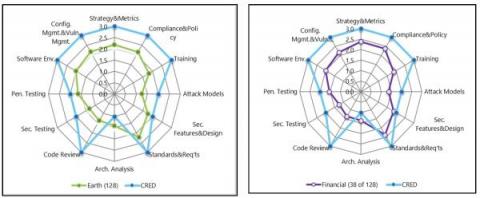
Spotlight on CRED: Benchmarking security with a BSIMM assessment
Better detections with YARA + LimaCharlie (Part 1)
One of our core features at LimaCharlie is building an extensible platform that security teams can use to build a robust detection and response platform. One way we accomplish this is native integration with multiple types of detection engines and languages.
Extend Your SOC Team with 24/7 Remote OT Security
Some economic sectors may be hitting the brakes, but the cybersecurity talent shortage persists across all industries and shows no signs of abating – not while sophisticated cyberattacks continue to rise in number and complexity. The 2022 (ISC)2 Cybersecurity Workforce Study found that even as the global cybersecurity workforce is at an all-time high, it is still short by 3.4 million workers.
Understanding the Big Business of Cybercrime
Can You Ride Velero for Your Kubernetes Backups?
Modern containerized applications are increasingly born in the cloud and the big three managed Kubernetes services – Azure Kubernetes Service (AKS), Amazon Elastic Kubernetes Service (EKS), and Google Kubernetes Engine (GKE) – rule the skies. With more users picking managed services in public cloud as their preferred platform, self-managing a backup infrastructure in the cloud is an antithesis.
This Feels Scripted: Zeek Scripting and Splunk
I originally planned to write this story as a follow-up to another blog that SURGe released for CVE-2022-3602 and CVE-2022-3786 (aka SpookySSL). That blog mentions that we weren’t able to test with any malicious payloads yet, and as things go… After releasing that blog, we came across proof-of-concept exploits that weren’t detected by our searches.
Reputational Risk Mitigation
Simplify your procurement process and subscribe to Splunk Cloud via the AWS marketplace Unlock the secrets of machine data with our new guide All companies want to protect their reputation as any mishandling of it, either self-inflicted or via outside forces, can have a devastating impact. Mitigating reputational issues involves mitigating the risk that leads to them.
Are you CCRI ready?
Nobody likes getting audited or inspected. Well, almost nobody; there’s always one person who consistently blows the curve. They gleefully anticipate inspections because they know they’re going to get a glowing review. We all have names for that person, most of which shouldn’t be included in a business blog. But what if, (bear with me) we could be that person?
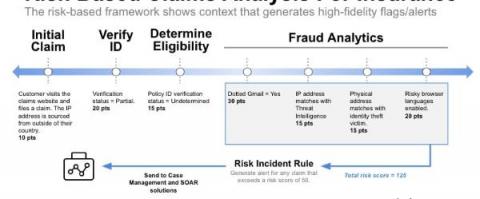
Tech-Forward Countermeasures in the Fight Against Identity Theft
Technology has expanded the avenues bad actors use to steal identities and sensitive data. However, digital tools are also giving users innovative countermeasures to protect themselves. Here are seven tactics anyone can use to help prevent identity theft.