Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
See technologies on the attack surface plus updates to Attack Surface Custom Policies and API keys
Keeping track of what technologies are being utilized across your attack surface has become virtually impossible as a result of the pace of innovation, developer methodologies, and many other factors. Questions such as, “Where am I hosting all of my WordPress sites? Or “What 3rd-party software is it using?” often go unanswered because of the sheer number of domains organizations now have to monitor.
Bypassing 2FA Authentication with Evilginx2
Due to the increasing number of cyberattacks, particularly zero days, organizations are scrambling to obtain the best security services available. While even the smallest organization might feel that implementing Two-Factor Authentication (2FA) will keep its data secure, a targeted attack from a nefarious threat actor could lure an employee into clicking and opening a malicious document.
Whoops! Researchers accidentally crash botnet used to launch DDoS and cryptomining campaigns
Researchers investigating a newly-discovered botnet have admitted that they "accidentally" broke it. In November, security experts at Akamai described a Golang-based botnet that they had discovered, hijacking PCs via SSH and weak credentials in order to launch distributed denial-of-service (DDoS) attacks and mine cryptocurrency.
The Increasing Threat Posed by Hacktivist Attacks: An Analysis of Targeted Organizations, Devices and TTPs
This year has seen an enormous increase in the number and claimed impact of hacktivist attacks on critical infrastructure and enterprises operating in critical services. Many attacks target unmanaged devices such as Internet of Things (IoT) and operational technology (OT) equipment. Attacks are motivated by geopolitical or social developments across the globe, with the goal of spreading a message or causing physical disruption.
How to prevent a rootkit attack before it is too late?
A rootkit is a malicious software program that helps cybercriminals infiltrate a system and take control. Hackers use rootkits to carry out espionage, data theft, deploy other malware such as ransomware, and all without leaving a trace. Once a rootkit is installed on a device, it can intercept system calls, replace software and processes and be part of a larger exploit kit containing other modules such as keyloggers, data theft malware, or even cryptocurrency mining malware.
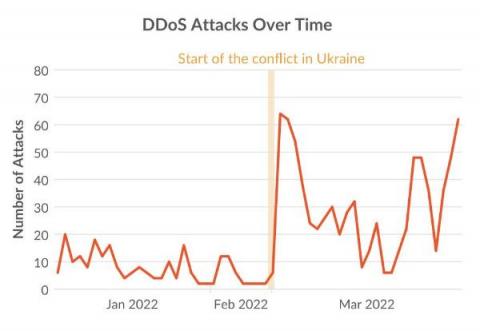
How the Russia-Ukraine conflict changed cyber attacks: More attacks, More DDoS
The conflict between Russia and Ukraine includes a cyberwarfare component with government-supported threat actors and civilian hacktivists taking sides. The goals of disrupting IT infrastructure and utilities have led to a 4-fold increase in DDoS attacks between 4Q21 and 1Q22. Over 150,000 volunteers have joined anti-Russian DDoS campaigns using container images from Docker Hub.
9 Steps to Mitigate Ransomware Attacks for Your Business
Ransomware attacks have become so prevalent in recent years that it’s no longer a matter of “if” your business may be the victim of a ransomware attack, but “when.” In fact, in 2021, 37% of global organizations reported that they were the victim of a ransomware attack. To mitigate the impact and probability of ransomware on your business, you must continuously look for new ways to secure your network and maintain continuous cybersecurity monitoring.
5 Tips for protecting your connected vehicle against Cyberattacks
As more connected vehicles hit the road, cyberattacks are increasing. Deloitte estimates that there will be over 470 million connected cars in use by 2025 if their popularity continues to grow at the current rate. And because each connected car produces about 25 GB of data every hour, they are a tempting challenge for cybercriminals and bad actors with malicious intent.
How Cyberwar is Wreaking Havoc on Small Businesses
As the world continues to change, so does the nature of warfare, where the Internet has become the main battleground for most of the world’s conflicts. But where is this headed? Cyberattacks have been around for much longer than you may think. The first worm was created by Bob Thomas in 1971: a malicious software that replicates itself, using some of the first world computers to spread to others.