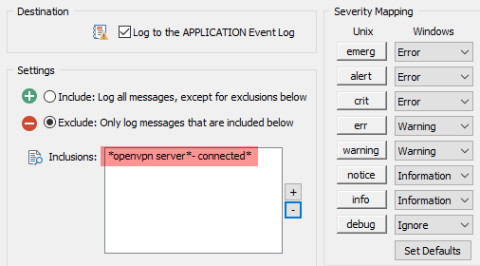
Announcing Graylog API Security v3.6
Graylog API Security v3.6 is here! Just taking the version number by itself, v3.6 sounds like an incremental step forward. But the truth is that v3.6 isn’t just a release milestone; it’s a huge inflection point in our mission to improve API security. There are multiple “firsts” in v3.6, which makes the total combination even more exciting.