Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
December 2021
Will Zero Trust Shape the Future of Cloud Security?
Zero trust is everywhere, and it will change the way we undertake security. Just as zero trust concepts are shaping the data center and our networks, they will shape cloud environments, as well. Many of the challenges of cloud security arose because we moved workloads to the cloud with no clear idea of how to secure them. Zero trust provides exactly those ideas.
Netskope Advanced Analytics Simplify Risk Management Across Roles (Part 2)
The following is the second part of a two-part series describing several critical use cases where Advanced Analytics can help teams make the right decisions to strengthen their overall posture and effectively manage risk.
Cloud Security Posture Management
What Financial Services Companies Need to Know About Infrastructure Access
Ding. That is the sound of the elevator opening on the ground floor of the One WTC building in New York. We’re both there for a meeting. You, as Director of Systems Engineering for a Financial Services provider, are presenting your plans to shore up the hybrid infrastructure used to run the bank’s new crypto-based services. I’m meeting with clients who are trying to rebuild their reputation, and SOC2 certification, after a data breach.
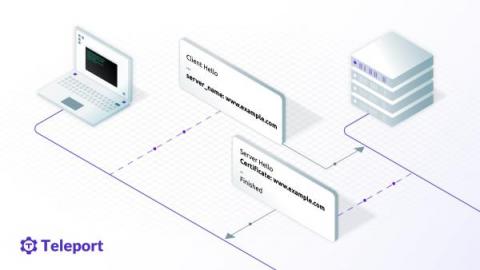
Leave SSL in the Dust, Turbocharge TLS with ALPN and SNI
As part of Teleport 8 we’ve made significant improvements to our routing, so much so the improvements have become a feature. Teleport 8 has new TLS routing that greatly reducing the port requirements needed for Teleport to run. Reducing the open network footprint down to a single port for your entire infrastructure and minimizing the attack surface. Want to know how we did it? Read on!
Security Service Edge (SSE) Considerations for the Future of Work
As we all learn how to practically apply the emerging technology of Secure Service Edge (SSE), here is a significant SSE use case—perhaps the most significant, at least in our immediate future. Looking ahead to 2022, many businesses will no doubt have return-to-office plans at the front of their minds. But coming back to the office brings its own unexpected risks that security leaders need to be ready for.
The Cloud Controls Matrix - what you need to know
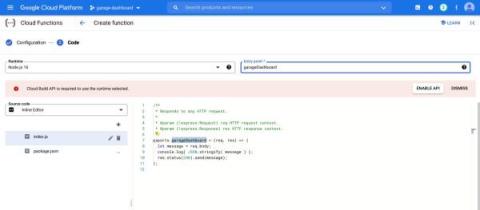
Cloud Function Dashboard with LimaCharlie
LimaCharlie provides everything you need to run modern cybersecurity operations, and it is also a great tool for builders. Our powerful web application is built using the publicly accessible API. There are no magic functions and we put the full power of the platform into the hands of those capable of wielding it. To demonstrate the kind of thing a user can easily build with LimaCharlie we have put together an interactive, embeddable dashboard.
How to Find and Eliminate Blind Spots in the Cloud
Pfizer IP Leak Isn't Unique. Protect Your Cloud Data With Proactive Encryption.
The pharmaceutical company Pfizer recently acknowledged that thousands of internal documents were leaked, including trade secrets related to its COVID-19 vaccine. In a California lawsuit, Pfizer stated that a former employee had exfiltrated sensitive data to their personal cloud accounts and devices while they were still working there.
Top 12 AWS Security Tools You Should Know
Amazon Web Services (AWS) provides a large suite of security tools to protect workloads, data, and applications running on AWS cloud infrastructure. Among the 25 AWS-native security solutions, it’s challenging to figure out exactly what your organization needs and why. This article helps simplify your decision by overviewing the top 12 security tools and services offered by Amazon and their uses.
Top 12 AWS Security Tools You Should Know
Amazon Web Services (AWS) provides a large suite of security tools to protect workloads, data, and applications running on AWS cloud infrastructure. Among the 25 AWS-native security solutions, it’s challenging to figure out exactly what your organization needs and why. This article helps simplify your decision by overviewing the top 12 security tools and services offered by Amazon and their uses.
Automate Your Cloud Operations With Humio and Fylamynt
A new API integration for Humio and Fylamynt helps joint customers improve the efficiency of their cloud operations teams by automating repetitive and manual operations tasks. Fylamynt, a low-code platform that delivers a developer’s approach to ITOps with site reliability engineering (SRE), works with Humio to empower faster response times to critical operational issues, reduce human error and increase productivity so DevOps teams can focus on adding value through innovation.
Khonsari: New Ransomware Delivered Through Log4Shell
While many organizations are patching the two recent Apache Log4j vulnerabilities (CVE-2021-44228 and CVE-2021-45046), attackers have been racing to exploit them to deliver malware, such as botnets, backdoors, and cryptominers. Among the threats delivered using Log4Shell exploits, a new ransomware family was found by Bitdefender: Khonsari.
What is CSPM (Cloud Security Posture Management)?
Cloud Security Posture Management (CSPM) is a category of cybersecurity tools that enhance cloud data security. CSPM is a relatively new concept, emerging from the ongoing rise of organizations moving their legacy workflows to the cloud.
Build securely with Snyk and GKE Autopilot
Speak with any customer in tech and the word Kubernetes will surely find its way into the conversation at some point or another. In terms of orchestration, automating deployments, scaling, managing containerized applications to meet growing customer demand, Kubernetes provides users with extensibility and flexibility.
Visibility and Security for GKE Autopilot
GKE Autopilot from Google Cloud is a mode of operation in Google Kubernetes Engine (GKE) designed to simplify working with Kubernetes in the cloud. Pairing secure DevOps practices with GKE Autopilot will help you and your teams ensure the security, compliance, and performance of your workloads and applications. Sysdig has collaborated with Google Cloud to enable visibility and security for GKE Autopilot and your containers.
Getting started with Teleport Desktop Access for Windows Servers
Introducing Teleport Desktop Access
Netskope Named One of the 25 Highest Rated Private Cloud-Computing Companies to Work For
Here at Netskope, our corporate culture means everything to us. In our core values, we strive to be collaborative and transparent, to cut out politics and bureaucracy, and to always have fun. With all of these values in mind, we are so excited to announce that Netskope has been named one of Battery Venture’s 25 Highest Rated Private Cloud-Computing Companies to Work For!
Teleport 8 - Introducing Desktop Access
If your organization runs cloud-native workloads on a mixed infrastructure of Linux and Windows, this announcement of Teleport 8 is for you! TL;DR Teleport 8 enables easy and secure remote access to a mixed fleet of Linux/SSH and Windows/RDP hosts via a single TCP/IP port. Before we dive deeper into how it works, let’s introduce Teleport to new readers of this blog.
Security risks of Cloud Computing | Threats, Issues and Challenges
Choosing an SSH Client on Windows
In today’s IT environments, operating systems blend into each other. In on-premises and hybrid or public cloud scenarios, Windows clients connect to Linux-based web servers and Kubernetes containers or microservices. There are several Windows-friendly SSH clients available to keep these connections secure.
Understanding the Netskope Chrome OS and Chromebook Integration
What comes to mind when you think of security “out-of-the-box?” You’re probably looking for something that will keep users as secure as possible while minimizing implementation friction points to your users. And with ransomware, malware, and phishing threats spreading faster and costing businesses more each year, IT teams must take a full-stack approach to defend against external attacks and internal vulnerabilities, while keeping the business running.
Cloud Threats Memo: Hard Statistics About Poorly Secured Cloud Accounts
Cloud accounts continue to be a valuable target for cybercriminals: not only do the resources of a compromised IaaS environment grant an immediate profit for the attackers, but the same infrastructure also provides a trusted environment to launch attacks against other targets.
Threat news: TeamTNT stealing credentials using EC2 Instance Metadata
The Sysdig Threat Research Team has detected an attack that can be attributed to the TeamTNT. The initial target was a Kubernetes pod exposed outside the network. Once access was gained, the malware attempted to steal AWS credentials using the EC2 instance metadata. TeamTNT is a threat actor that conducts large-scale attacks against virtual and cloud solutions, like Kubernetes and Docker.
Correctly Configure Your Clouds: It's More Than Just Settings
Gartner made an interesting prediction just a few years ago: “Through 2025, 99% of cloud security failures will be the customer’s fault.” Practically every single cloud security failure can be fairly described as a misconfiguration of one kind or another. The 2025 end is kind of arbitrary, really; the prediction is likely to be true until the end of time. In my previous article, I discussed targeting these misconfigurations at their root.
How to Pass a FedRAMP Audit for SaaS Providers: Part 2
In our last blog post How to Pass a FedRAMP Audit for SaaS Providers: Part 1 , we looked at what FedRAMP is and why it matters for SaaS providers. We also discussed a success story with one publicly traded Teleport SaaS customer who used Teleport to pass their FedRAMP audit.
Introducing Rubrik SaaS Support for Microsoft Azure SQL
Since January 2020, Microsoft Azure SQL DB has grown nearly 3x in popularity. This rapid growth comes as no surprise as Platform-as-a-service (PaaS) offerings have many benefits in the migration strategy from traditional SQL Server database workloads. The Microsoft PaaS offering, Azure SQL Database, takes care of mundane tasks once performed by Infrastructure Engineers such as patching operating systems and applying SQL Server updates or critical security patches.
It's Time for the U.S. Federal Government to Move (FAST) on Cloud Security and Zero Trust
Executive Order 14028 on Improving the Nation’s Cybersecurity was released in May with nine sections outlining specific focus areas for security improvements. As we noted at the time, Netskope applauded the EO for how it placed significant emphasis on zero trust security adoption, mentioning it no fewer than 11 times, and insisting on proactive action.
Using Teleport to Secure SSH and Kubernetes Access
Over-Privileged Service Accounts Create Escalation of Privileges and Lateral Movement in Google Cloud
In this blog, we’ve analyzed data from Netskope customers that include security settings of over 1 million entities in 156,737 Google Cloud (GCP) projects across hundreds of organizations (see Dataset and Methodology for more details on the dataset). We will specifically look at the configuration of service accounts, see what’s commonly occurring in the real world, and analyze how multiple security misconfigurations can lead to escalation of privileges and lateral movement.
NIST's Definition of Cloud Computing
How to Pass a FedRAMP Audit for SaaS Providers: Part 1
You work at a SaaS provider, and now you need to pass a FedRAMP audit. If that describes you, read on. This post will tell you (almost) everything you need to know about how to pass a FedRAMP Audit. For the rest, reach out to us. We will put you in touch with one of our Solution Engineers like me who have helped some of the largest SaaS providers in the world pass their FedRAMP audit prior or after IPOing. It’s what we do.