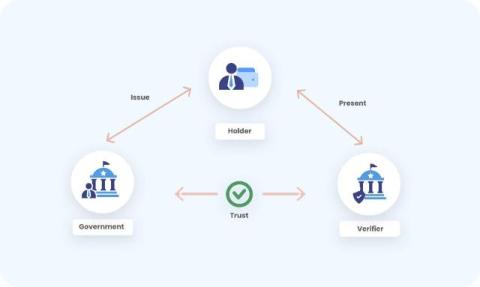
How to Avoid a Data Breach: Best Practices for SOC 2 Compliance
In this guide, you're going to learn how to avoid devastating data breaches by becoming SOC 2 compliant. You'll gain the ability to safeguard sensitive customer data, build unshakable client trust, and position your business as a fortress against cyber threats. No more sleepless nights worrying about hackers exposing Social Security Numbers, bank accounts, or proprietary information - or worse, watching your reputation crumble after a breach.