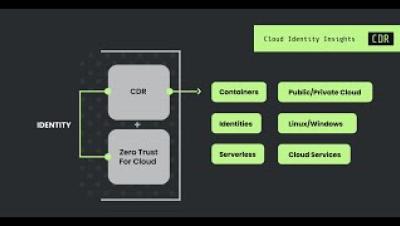
Cloud identity insights - Detect at the edge in real time
Cloud attacks strike fast. Prevention used to be enough, but not anymore. And legacy EDR tools fall short because they lack visibility into cloud identities and behavior. Defenders need the ability to detect at the edge - in real time - and correlate early stage identity behavior to see what's happening fast.