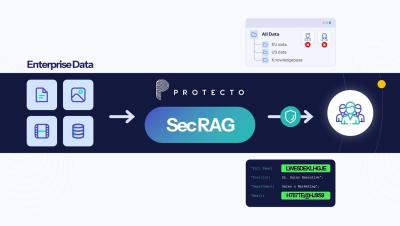
Reducing Tool Sprawl
JumpCloud’s MSP partners are at the forefront of providing essential IT services to small and medium-sized businesses globally. In our interview series, we delve into conversations with these partners, exploring the dynamics of their MSPs and how JumpCloud plays a pivotal role in their operations. In today’s feature, we had the opportunity to speak again with Chris McKewon of Xceptional.