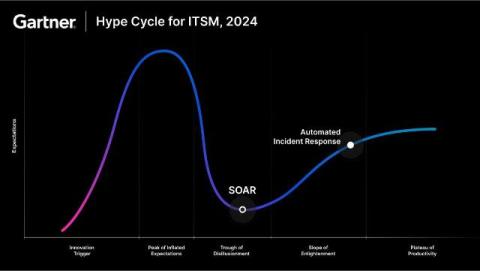
The Best Proxy Servers for Multi-Accounting
Business owners are increasingly recognizing its positive impact on business growth. Many marketing and sales strategies use different accounts on a single platform. However, despite its effectiveness in business, not all platforms allow multi-accounting. That’s where residential proxy comes in as an effective solution for multi-accounting.