Climbing the Vulnerability Management Mountain: Reaching Maturity Level 4
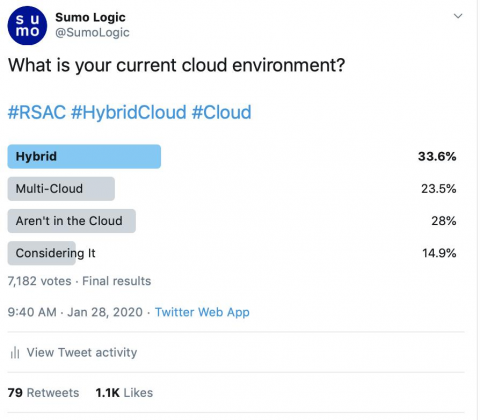
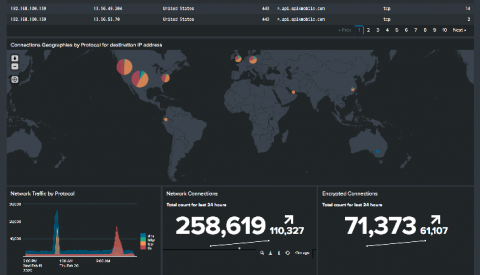
The climb is getting steeper, but thanks to hard work, vision and insight are much keener. At ML:4, all assets are scanned by a combination of agent and remote scans on a normal cadence. This will generate a lot of data dictated by threat and patch priority. Thousands of new vulnerabilities are released each year, and no company or product can detect all of them. Organizations must prioritize their coverage of vulnerabilities that they determine will have the biggest impact.