Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Data Privacy Solutions: How to Choose the Right One
Data privacy solutions are crucial for complying with privacy regulations and maintaining security. In the first nine months of 2019, there were 5,183 reported data breaches, with 7.9 billion records exposed, according to the Data Breach Quickview. Modern regulations, such as GDPR and CCPA, require companies to develop reasonable data protection measures to protect consumers’ personal information against exposure or loss.
Annotate and Fill Out PDF Files Directly With the Egnyte Mobile App
Working on PDF documents on mobile devices has been one of the most anticipated features this year. Now, with the integration of PSPDFkit, Egnyte has added this capability to its iOS app (the Android app has this feature in Beta, and it will be launched officially later this fall) Users who work on PDF files now have the tools for fast and easy editing. It reduces the time needed for file preparation as you can do it on the go within one app. It also reduces the costs of annotations.
A DLP Security Checklist for IT Professionals
As of June 2020, more than 3.2 million consumer records were exposed in the 10 biggest data breaches this year. Eight of the ten largest breaches occurred at healthcare or medical organizations, meaning patient information in addition to PII was likely acquired by hackers. Data loss prevention (DLP) is an ever-changing practice, with new security policies and information security standards evolving to keep up with the threat of online hackers.
Easy Ways to Boost Employee Productivity Remotely
Employee monitoring and productivity tracking features valuable insights into your teams’ performance levels throughout the day. If your office has been recently affected by the COVID-19 pandemic, you might also be transitioning into a more remote-friendly workplace environment. How do you make sure your employees are staying productive? Can you accurately measure an increase or decrease in your team’s overall productivity?
Under pressure: Managing the competing demands of development velocity and application security
The first software development team I worked on operated on the follow mantra: Make it work. Then, make it fast. Then, make it elegant (maybe). Meaning, don’t worry about performance optimizations until your code actually does what it’s supposed to do, and don’t worry about code maintainability until after you know it both works and performs well. Users generally have no idea how maintainable the code is, but they do know if the application is broken or slow.
BYOD security explained: what is a BYOD policy?
Bring your own device (BYOD) describes the practice of using a personal device such as a smartphone or tablet to conduct business on an organization's network or with its data. Organizations constantly walk a tightrope with their BYOD policies to balance employee productivity and satisfaction against the effective management of cybersecurity risks.
Black Box Testing: What You Need to Know
Today’s software development life cycle includes a variety of quality and security testing techniques at every stage. Frequent testing throughout the DevOps pipeline is imperative considering the ever-increasing pace of development. One of the most common testing methods that companies use to ensure the products they are pushing out are secure and high-quality is black box testing.
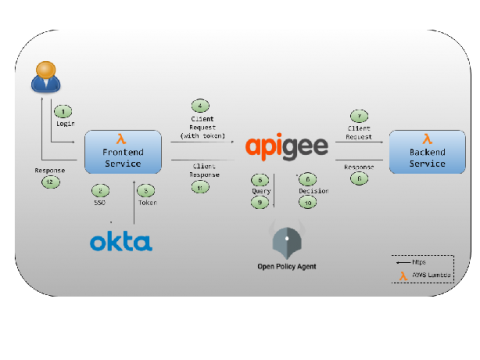
API Authorization at the Gateway with Apigee, Okta and OPA (Part 1)
API gateways have become a standard component in modern application architectures. The gateway exposes application APIs to the Internet and serves as a logical place to enforce policy. This is a two-part series about enforcing API authorization policies in Apigee with Okta as the identity provider (IdP).
Watch Here: Using Analytics to Measure AppSec ROI
Maximizing the value of your application security (AppSec) analytics not only provides a window into whether or not you’re meeting security requirements but also it helps you prove your ROI. That can be a challenge for a lot of organizations – when stakeholders are not close to the data, they may miss milestones like hitting goals for reducing security debt or even how much AppSec program has matured by data.