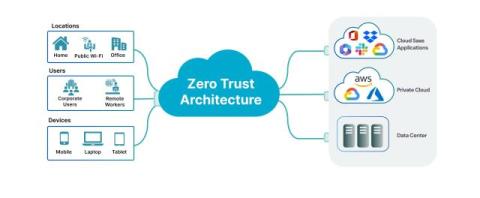
How to Detect Threats to AI Systems with MITRE ATLAS Framework
Cyber threats against AI systems are on the rise, and today’s AI developers need a robust approach to securing AI applications that address the unique vulnerabilities and attack patterns associated with AI systems and ML models deployed in production environments. In this blog, we’re taking a closer look at two specific tools that AI developers can use to help detect cyber threats against AI systems.