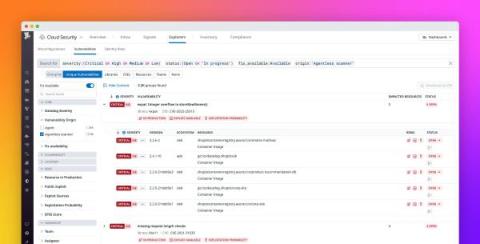
Monitor AWS WAF activity with Datadog
In Part 2 of this series, we looked at Amazon’s built-in monitoring services for AWS WAF activity and audit logs. In this post, we’ll demonstrate how Datadog complements your WAF’s existing protection and extends its capabilities to not only offer protection at the perimeter but also to the APIs and services within your network.