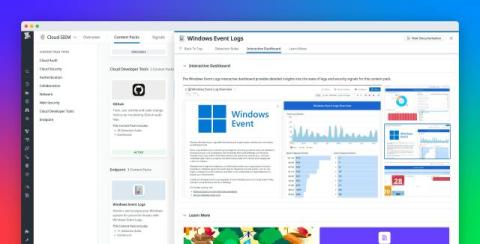
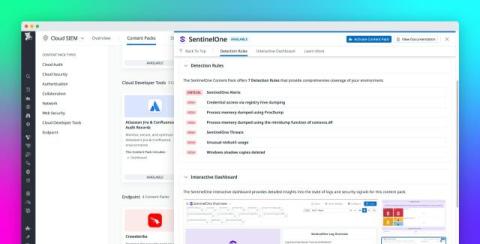
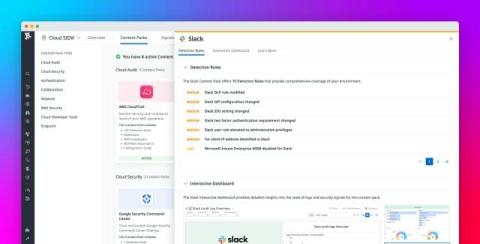
Monitor your Windows event logs with Datadog Cloud SIEM
Windows event logs are a key source of important information about your Windows environments, including detailed records of user activities, system performance, and potential security issues. However, with the sheer volume of logs modern environments generate, it can be overwhelming for security teams to efficiently detect, triage, and respond to threats in real time.