Monitor highly regulated workloads with Datadog's FIPS-enabled Agent
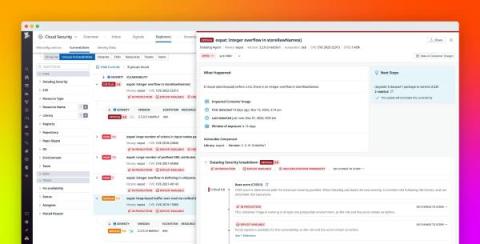
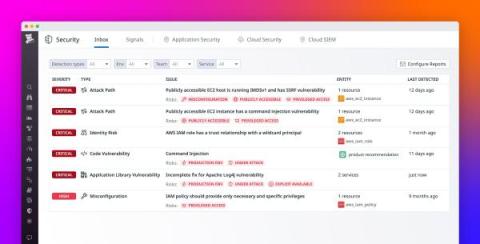
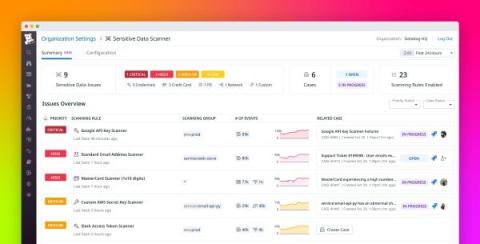
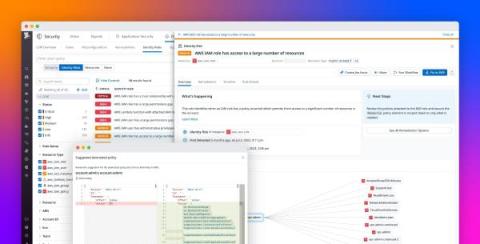
Protecting sensitive data from the threat of exposure is a non-negotiable business imperative for organizations, especially those in highly regulated sectors like government and healthcare. To help organizations keep their data secure, the National Institute of Science and Technology (NIST) developed a set of requirements for the hardware and software components responsible for data encryption.