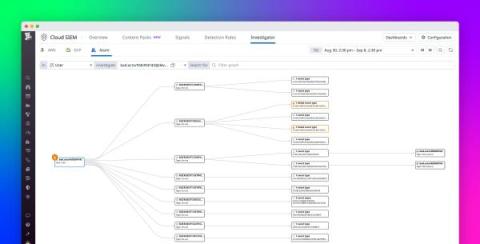
Visualize activity in your Azure environment with Datadog Cloud SIEM Investigator
Cloud infrastructures can comprise thousands of interconnected and dynamic resources. This complexity introduces unique challenges to monitoring and securing these architectures. Understanding where user activity originates—and what actions constitute security threats—is a complex task when you’re dealing with the huge volume of logs, metrics, and other telemetry that highly distributed cloud environments generate each day.