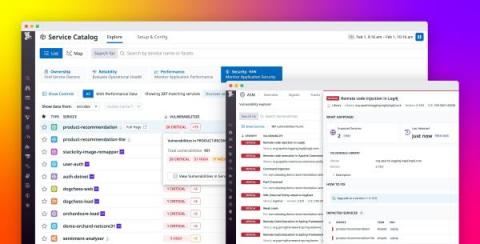
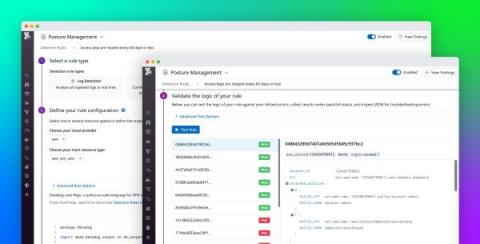
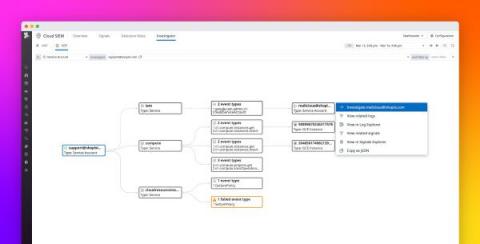
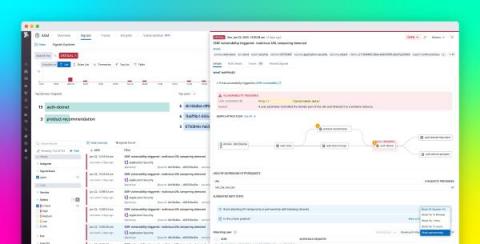
Gain visibility into open source vulnerabilities with Datadog Application Vulnerability Management
Open source libraries have become an indispensable part of modern applications. Approximately 90 percent of organizations use open source software to support their services, but monitoring these dependencies can be difficult when environments run thousands of ephemeral services.