Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Datadog
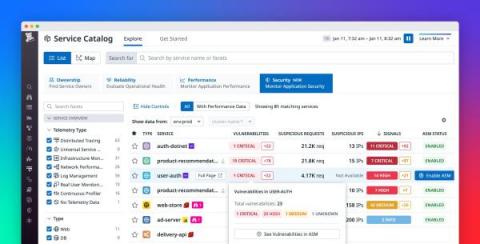
Gain visibility into risks, vulnerabilities, and attacks with APM Security View
As your business grows and your services scale in number and complexity, it’s difficult to maintain a rapid pace of innovation while keeping your applications secure. It’s particularly challenging to respond to attacks, as DevOps and security teams need to collaborate to understand each attack’s root cause and remediate the vulnerabilities that enabled it.
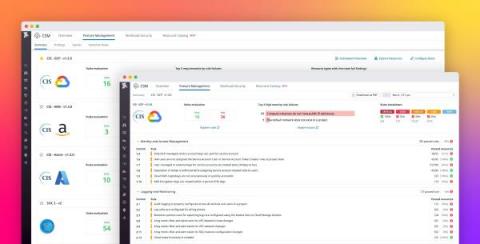
Improve the compliance and security posture of your Google Cloud environment with Datadog
Organizations are scaling their environments at a rapid pace, deploying thousands of cloud resources, services, and accounts. Because of their size and complexity, these environments are more susceptible to compliance issues—a misconfiguration in a single cloud resource can lead to costly data breaches. For that reason, organizations are prioritizing governance, risk, and compliance (GRC) management to ensure that their environments are configured appropriately.
Best practices for application security in cloud-native environments
Editor’s note: This is Part 3 of a five-part cloud security series that covers protecting an organization’s network perimeter, endpoints, application code, sensitive data, and service and user accounts from threats. In Parts 1 and 2 of this series, we discussed the importance of protecting the boundaries of networks in cloud environments and best practices for applying efficient security controls to endpoints.
This Month in Datadog: Cloud SIEM Investigator, API Catalog, Expanded AWS Coverage, and more
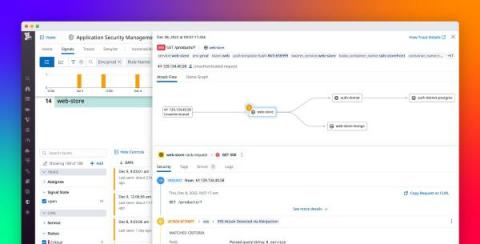
Secure serverless applications with Datadog ASM
The popularity of serverless architectures continues to grow as organizations seek ease of scalability and to eliminate the need to provision and manage infrastructure. In fact, in our most recent State of Serverless report, we found that more than half of our customers have adopted serverless technologies offered by Azure, Google Cloud, and AWS.
How Firstup extends security organizational wide with Datadog and AWS
Highlights from AWS re:Invent 2022
Just like shopping on Black Friday, AWS re:Invent has become a post-Thanksgiving tradition for some of us at Datadog. We were excited to join tens of thousands of fellow AWS users and partners for this annual gathering that features new product announcements, technical sessions, networking, and fun. This year, we saw three themes emerge from the conference announcements and sessions.
Fix common cloud security risks with the Datadog Security Labs Ruleset
With the continual increase of attacks, vulnerabilities, and misconfigurations, today’s security organizations face an uphill battle in securing their cloud environments. These risks often materialize into unaddressed alerts, incidents, and findings in their security products. However, part of the issue is that many security teams are often stretched too thin and overburdened by alert fatigue.
Fix common cloud security risks with the Essential Cloud Security Controls Ruleset
With the continual increase of attacks, vulnerabilities, and misconfigurations, today’s security organizations face an uphill battle in securing their cloud environments. These risks often materialize into unaddressed alerts, incidents, and findings in their security products. However, part of the issue is that many security teams are often stretched too thin and overburdened by alert fatigue.