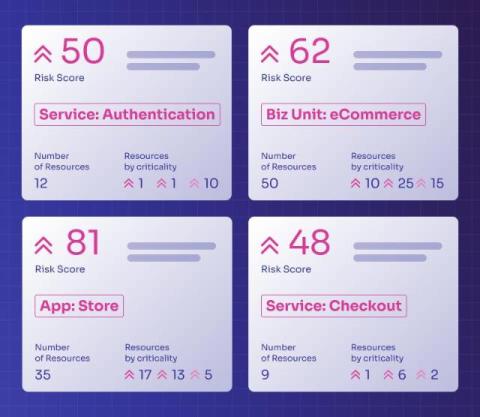
AWS & 1Password: New integrations help strengthen security
When the tools in your security stack work together, it reduces administration overhead, lowers costs, and increases protection across your organization. That’s why we’ve spent the last year deepening our partnership and product integrations with AWS and other security providers in their ecosystem.