Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Supply Chain
Identifying and Avoiding Malicious Packages
Pyrsia: Decentralized Package Network that Secures the Open Source Supply Chain
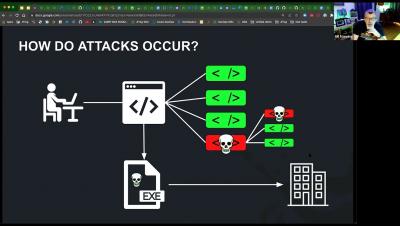
Supply chain security has received a lot of attention in recent years. And rightly so. Software vulnerability exploitation attacks have been a key tool in the hands of the hackers to hamper businesses, compromise sensitive data, and a cause of general sense of fear around open source software.
Pyrsia: Open Source Software that Helps Protect the Open Source Supply Chain
Stephen Chin is no stranger to having big ideas and implementing them to help the developer community. In the last twenty years he’s been involved in building open source IDEs, bootstrapping rich client libraries, maintaining JVM languages, and cultivating relationships with developers that do the same.
Everything You Need to Know to Prevent JavaScript Supply Chain Attacks
JavaScript supply chain attacks are a bit like rolling thunder. The boom starts in one location and then reverberates along a path, startling folks, shaking windows, and—if there is a significant enough storm to accompany the thunder—leaving varying degrees of devastation in its wake.
What Is Software Supply Chain Security?
Most software today isn’t developed entirely from scratch. Instead, developers rely on a range of third-party resources to create their applications. By using pre-built libraries, developers don’t need to reinvent the wheel. They can use what already exists and spend time on proprietary code, helping to differentiate their software, finish projects quicker, reduce costs, and stay competitive. These third-party libraries make up part of the software supply chain.
GitHub Supply Chain Attacks Highlight the Urgency of Zero Trust SaaS Data Security
In early April, the tech industry witnessed a major GitHub security incident targeting GitHub organizations using Heroku and Travis CI. GitHub was made aware of this threat via an attack leveraging AWS API keys to GitHub’s own npm production infrastructure. As upstream security risks within SaaS platforms become more common, organizations that leverage these platforms are relying on tools like Nightfall to protect themselves.
The TTPs of JavaScript Supply Chain Attacks
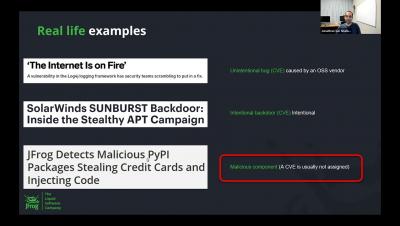
Recent research studies demonstrate that software supply chain attacks are on the upswing—by almost 300% in 2021 alone. To avoid attacks related to open-source libraries and JavaScript, businesses need to understand the tactics, techniques, and procedures (TTPs) associated with JavaScript supply chain attacks.
Securing the Digital Supply Chain Ep. 10 - Peeyush Ranjan
Software Supply Chain Security: The Basics and Four Critical Best Practices
Enterprise software projects increasingly depend on third-party and open source components. These components are created and maintained by individuals who are not employed by the organization developing the primary software, and who do not necessarily use the same security policies as the organization. This poses a security risk, because differences or inconsistencies between these policies can create overlooked areas of vulnerability that attackers seek to exploit.