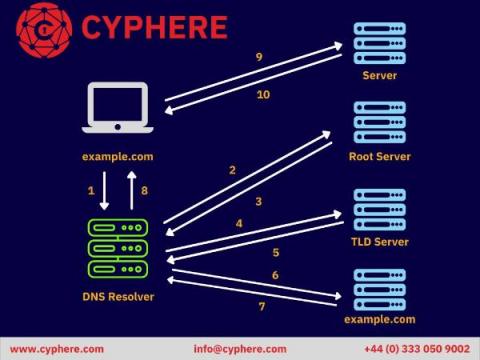
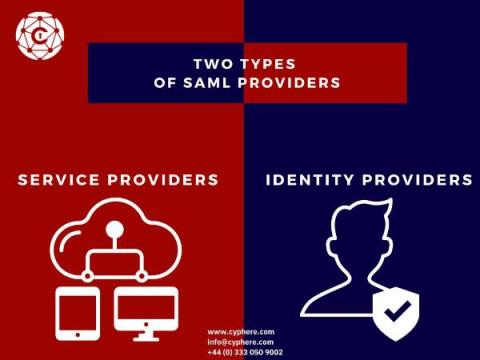
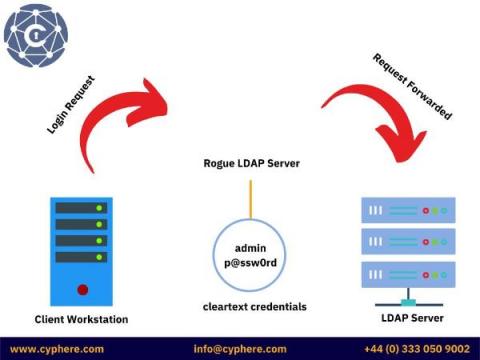
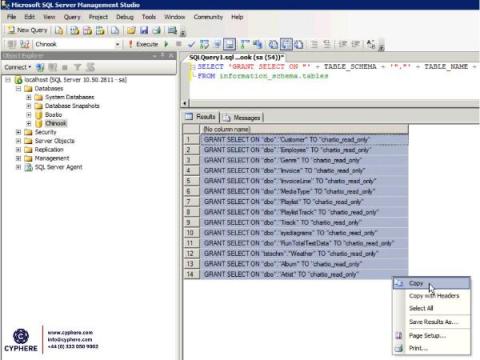
Benefits and Risks of Social Media
Social media can be a great way to stay connected with friends and family, but it also poses risks. In this blog post, we will explore the dangers of social media for kids, teens, individuals and businesses as well as the benefits. We will talk about the social media risks and how to protect yourself from them. There are many ways that you can reduce your risk when using social media sites like Twitter or Facebook.