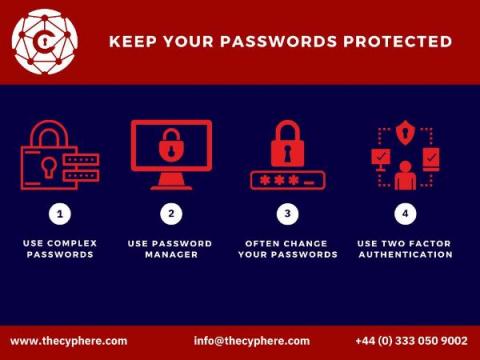
Data Protection Healthcare and Social Care | How to Store Information
The Data Protection Act is an important part of the cyber domain and legislation for anyone working in health and social care. It governs how to protect the information in health and social care. This blog post will explore the implications of the act on healthcare professionals, patients and other individuals who may have dealings with you as an organisation or individual providing care to others and the importance of protecting sensitive data in health and social care.