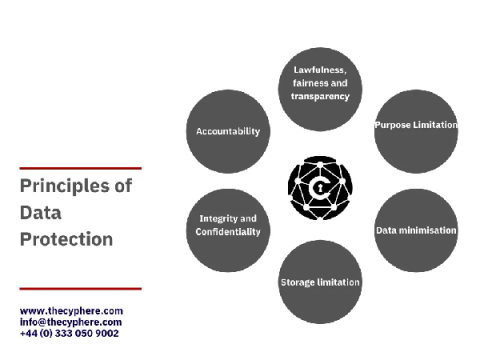
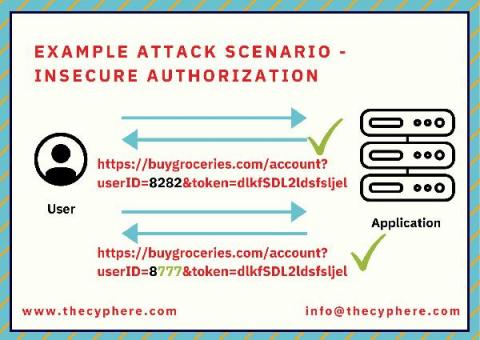
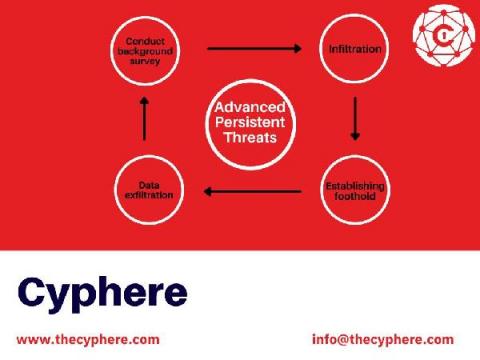
100+ Server Security & Best Practices Tips on Securing a Server
Servers are the backbone of an organisation’s IT infrastructure as they provide both information and computational services to its users. And because of their critical role, servers are always a prime target for hackers looking to exploit any vulnerability they can find, leading to data breaches and financial and reputational damage.