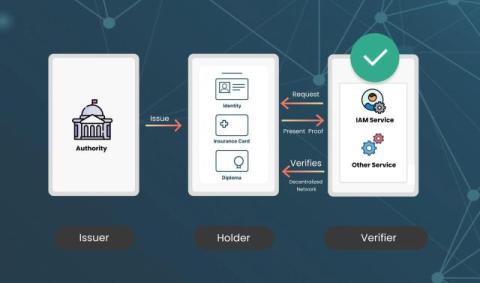
How to adapt firewall rules for medical device security in healthcare
Healthcare has become more digitized; medical devices play an increasingly vital role in patient care. Alongside these advancements, any medical device connected to the internet can become a vulnerable entry point for cyberthreats. Hospitals and healthcare providers must take proactive steps to protect these devices, ensuring their reliability while safeguarding patient data and network integrity.