The Fundamentals of Windows Defender SmartScreen
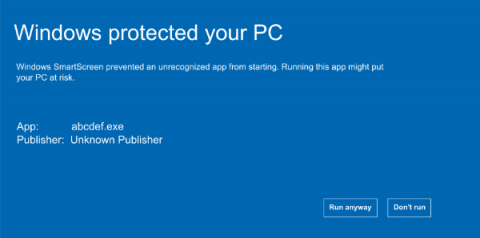
While purchasing the Code Signing Certificate, particularly EV Code Signing Certificate, we all came across the term Windows Defender SmartScreen. But, only a few understand the term correctly and purchase the right digital solution. SmartScreen has become a prominent security Windows OS security mechanism, helping users to prevent cyber threats. It blocks installations if it doesn’t recognize the publisher.