Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
Can WiFi See What You Search on Incognito?
Yes, your WiFi provider – also called an Internet Service Provider (ISP) – can see what you search and what sites you visit, even when you’re in incognito mode. The owner of the router will also be able to see what you search in the router logs. Incognito mode only prevents your site visits from being saved to your browser history. Read on to learn more about how incognito mode works and who can see your search history.
IPv6 Insights
Beyond the Basics: How Can Proxies Be Used?
New CISA Directive Highlights Vulnerabilities at Network Edge
After a wave of zero-day attacks targeting widely used security and networking appliances, the Cybersecurity & Infrastructure Security Agency (CISA) is taking new measures to protect Internet-exposed networking equipment.
Identifying BOD 23-02 Network Management Interfaces with Splunk
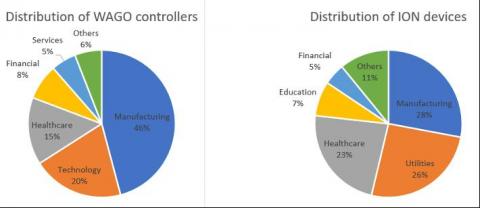
Extending visibility through our new ICS/OT collection
Increasingly, security teams are tasked with identifying, understanding, and managing risk around devices that may live outside the traditional IT umbrella. Operational Technology (OT) refers to computing systems that are used to manage and process operational functions as opposed to administrative operations, with Industrial Control Systems (ICS) being a major segment of that OT sector.
10 Out Of 10 SecOps Pros Agree: You Can't Secure What You Can't See
Network complexity is at an all-time high. Between legacy technology, hybrid-multi-cloud environments, and networks cobbled together by mergers and acquisitions, it’s impossible for people to keep track of the network, its topology, and behavior. The idea of trying to trace a path through a multi-cloud network seems akin to being asked to pull a rabbit out of your hat.
Forward Networks' Digital Twin Technology Named Best SaaS Solution by Cloud Security Awards
Lessons Learned from OT:ICEFALL - New Vulnerabilities and Insights on OT Security Design and Patching
In our final OT:ICEFALL report, Forescout Vedere Labs presents three new vulnerabilities and concludes the project after one year of research following the original disclosure. The OT:ICEFALL research, including 61 vulnerabilities affecting 13 vendors, has yielded three key insights into the current state of OT product security.