Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
Understanding network lifecycle management
Behind every important business process is a solid network infrastructure that lets us access all of these services. But for an efficient and available network, you need an optimization framework to maintain a strong network lifecycle. It can be carried out as a lifecycle process to ensure continuous monitoring, management, automation, and improvement.
Go Beyond Device Visibility to Prioritize and Act on Cybersecurity Risk
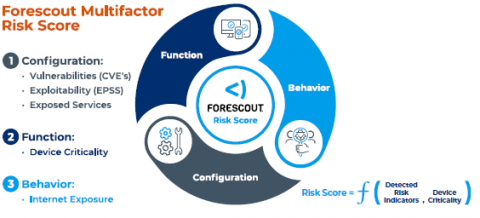
When I joined Forescout as CEO six months ago, I was excited to partner with our strong employees, management team and board as we take the company through its next phase of growth. Today I’m pleased to announce enhancements to the Forescout® Platform that will help customers fully understand the risk posture of their attack surface and enable their security teams to focus on remediating the assets that pose the most risk.
SNAPPY: Detecting Rogue and Fake 802.11 Wireless Access Points Through Fingerprinting Beacon Management Frames
I’ve always had a great love of all things wireless/RF for as long as I can remember. The ability to send frames/packets of data out into the world (the airwaves!) for anyone with the right equipment and looking at the right frequency to pluck them out and reconstruct them - amazing! I am still the proud owner of both ORiNOCO Gold and Silver PCMCIA cards, these two bad boys defined wireless hacking back in the early 2000’s.
5 Steps to Combating Emerging Threats with Network Security
In today’s rapidly evolving threat landscape, cybercriminals have become more sophisticated than ever, making it crucial to stay abreast of the latest trends and tactics. The challenge is exacerbated by the expanding attack surface as more devices and device types connect to enterprise networks: IT, OT, IoT and IoMT devices, all with known vulnerabilities that can be exploited.
What companies need to stay secure #shortvideo #automation #inspiration #success #instagram #tiktok
CVE-2023-33299: Critical Fortinet FortiNAC RCE Vulnerability
Fortinet Fortigate Vulnerability CVE-2023-27997: How to Surface Exposed Devices and Mitigate the Threat
Recently, a critical vulnerability tracked as CVE-2023-27997 was identified in Fortinet Fortigate appliances. Fortinet makes some of the most popular firewall and VPN devices on the market, which makes them an attractive target for threat actors. This vulnerability has been exploited by the Chinese APT group Volt Typhoon, among others, targeting governments and organizations worldwide. As a result, Fortinet has released an urgent patch for affected systems.
Take it From a Compliance Officer: Secure Networks Matter
Even before the fiasco at Silicon Valley Bank, financial institutions were under tremendous scrutiny from regulators. How could they not be? Banks are among the oldest known targets for theft, and in a digital age, the best way to extract money is going to be either straight cyber-theft from existing accounts or ransomware. IT systems that house customers’ financial data can be architected with the right security controls in place to protect that data to the highest standard.