Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
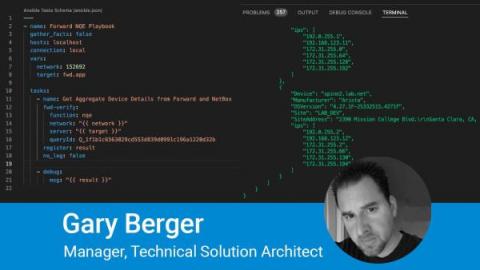
Forward Networks 22.5 Release adds external sources to provide a powerful data aggregation layer for comprehensive testing and integration.
We just released our 22.5 Release to Forward Enterprise and boy what a surprise to have our NQE external data sources finally ready to show the world. Very simply, this allows you to pull in data from external HTTP sources (currently we support HTTP GET) and automagically model the data in our data model explorer and our integrated development environment. To enable this you simply need to add the resource endpoints for the HTTP API of the data you are interested in. i.e.
What is a VPN? Types of VPNs and How They Work
As the number of remote workers grows, virtual private networks (VPNs) are becoming a popular way to grant remote access to employees while hiding online activities from attackers. With a VPN, your organization can secure network traffic between your site and users by creating an end-to-end secure private network connection over a public network. In this article, you will learn how a VPN works, what protocols are needed, what challenges are involved, and what alternatives are available.
A Hospital's Cybersecurity: 10 Steps to Help Ensure Patient Safety and Continuous Operations
Across a health system’s digital terrain, the most vulnerable assets are connected medical devices. If those devices become compromised, the infiltration could impact a patient’s privacy, health and safety. Moreover, it could shut down care delivery for days, weeks or longer, with long-lasting financial and reputational impacts. According to Deloitte, an estimated 70% of medical devices will be connected by 2023.
Wi-Fi Network Definition and Importance
Nowadays, Wi-Fi networks are among the most commonly used networks, making them a go-to target for cyber attacks. An attacker with basic tools and knowledge can crack 70% of Wi-Fi networks.
Dissolving Operational Security Challenges in a Hybrid Cloud Environment
Forescout Continuum - What's New - Q1 22 Release
How to detect TOR network connections with Falco
TOR was created with the idea of anonymizing connections across the Internet, but as in other instances, this can be used by attackers to hide themselves. In this article, we will describe how easy it is to detect inbound and outbound network connections through the TOR network using Falco.
A Hospital's Cybersecurity: 10 Steps to Help Ensure Patient Safety and Continuous Operations
Across a health system’s digital terrain, the most vulnerable assets are connected medical devices. If those devices become compromised, the infiltration could impact a patient’s privacy, health and safety. Moreover, it could shut down care delivery for days, weeks or longer, with long-lasting financial and reputational impacts. According to Deloitte, an estimated 70% of medical devices will be connected by 2023.
Corelight Investigator accelerates threat hunting
This morning we announced Corelight Investigator, an open NDR platform that enables security teams with the next-level evidence they need to disrupt attacks and accelerate threat hunting through an easy-to-use, quick-to-deploy SaaS solution. How does it work? Investigator combines battle-tested network evidence with intelligent alert scoring to deliver prioritized alerts tied to correlated evidence, enabling analysts to cut through the queue and accelerate incident response.