New Connectivity Insight for SecOps and NetOps
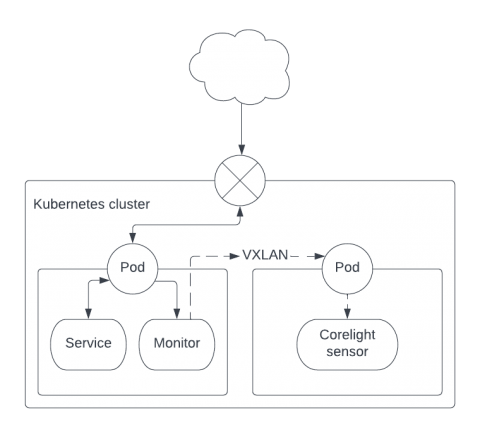
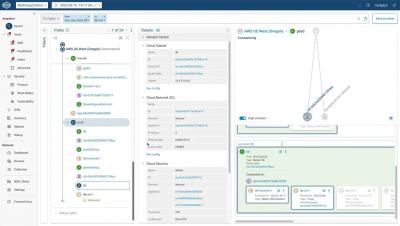
Last June, Forward Networks announced several enhancements to the platform designed to help SecOps teams prove compliance, automate CVE (critical vulnerability exposure) responses, and remediate threats quickly. Today, we’re happy to share that we’ve continued to build out our security use cases by adding new functionality to our security posture security matrix (previously known as zone-to-zone security matrix) and delivering Layer 7 application connectivity analysis.