Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
Wi-Fi and its relationship with the zero-trust model
Zero-trust network architecture (ZTNA) provides a holistic view of business cybersecurity that secures your applications and environment when accessed by any user, device, or location. A comprehensive zero-trust model enables you to mitigate, detect and respond to threats.
Demo: Firebox Management in WatchGuard Cloud: Branch Office VPN (BOVPN)
Why Microsegmentation is Still a Go-To Network Security Strategy
Prof. Avishai Wool, AlgoSec co-founder and CTO, breaks down the truths and myths about micro-segmentation and how organizations can better secure their network before their next cyberattack.
Unify endpoint and network evidence
What does XDR mean for your organization?
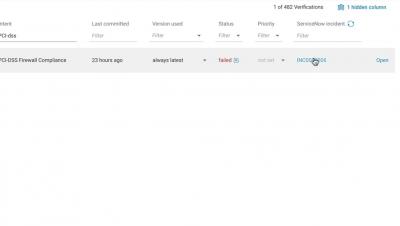
Proactive Compliance Verification for Network Security
UNDER PRESSURE: Enterprise IT Teams Use NQE To Reduce Time-Intensive Processes
Today's enterprise IT teams are well acquainted with the pressures of ensuring network security, while also managing the time it takes to do so. The recent experience of one multinational technology company perfectly illustrates how Networks Query Engine (NQE) can be used to quickly and effectively bolster network security. As with most companies, this company's IT team was asked on a regular basis to locate IP addresses in the network.
How to Achieve Network Infrastructure Modernization
ALPHV: Breaking Down the Complexity of the Most Sophisticated Ransomware
In our new threat briefing report, Forescout’s Vedere Labs describes how it analyzed files and tools used by an affiliate of the ALPHV ransomware group during an attack. ALPHV, also known as Black Cat, is a Ransomware-as-a-Service gang that was first discovered in November 2021.