Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
5 Steps to Unsticking a Stuck Network Segmentation Project
Digital transformation has ushered in interconnected networks that enable information sharing and collaboration. That’s great for efficiency and productivity, but many networks are flat, leaving organizations susceptible to cyberthreats that can move laterally, even across distributed environments, enabling hackers to exploit openings and pivot into their most valuable data.
Breaking down firewalls with BPFDoor (no e!) - How to detect it with Falco
BPF (not eBPF), typically viewed from a defender/sysadmin’s perspective, provides easy access to network packets and the ability to take actions via programs written based on custom filters BEFORE they ever reach a (local) firewall. This same power, according to the PWC report and pending conference talk, was leveraged by a threat actor named Red Menshen, where the attackers have used BPFDoor technique to gain stealthy remote access to compromised devices from at least 2018 to the present.
Not all "Internet Connections" are Equal
People commonly think that any “Internet Connection” is exactly the same, or they may be vaguely aware that some connections are faster than others. However, there are significant differences between the connections. While these differences may not matter to someone who just wants to browse websites and read email, they can be significant or even showstoppers for more advanced users or s. This is especially true for anyone looking to do security testing or vulnerability scanning.
Enhanced Network Evidence for the Modern SOC
Forescout and Cysiv: Threat Detection Across Your Digital Terrain
Today marks an exciting moment in time for our customers and partners. Today, Forescout announced its intent to acquire Cysiv, a company with deep expertise in data-powered threat detection and response.
Forward Networks Adds New Verification Capabilities To Make Hybrid Multi-cloud Networks More Secure
Killnet: Analysis of Attacks from a Prominent Pro-Russian Hacktivist Group
In our new threat briefing report, Forescout’s Vedere Labs leverages a list of IP addresses known to be used by Killnet hacktivists during past attacks to study their TTPs when attacking a series of honeypots we control.
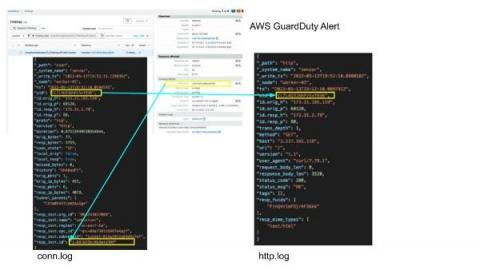
Enriching NDR logs with context
In this post, we show how enriching Zeek® logs with cloud and container context makes it much faster to tie interesting activity to the container or cloud asset involved.In cloud or container environments, layer 3 networking is abstracted away from the higher-level tasks of running workloads or presenting data. Because of this abstraction, when Zeek logs are collected for cloud or container network environments, the attribution of a network flow to actual workload or application is difficult.
Rapid7 Integration Makes Forward Networks the Only Digital Twin that Provides End-to-End Security Posture Visibility
There is no shortage of alerts concerning security vulnerabilities. Unfortunately, the deluge of data available is overwhelming and not specific enough to be actionable. We don’t think that’s very helpful, so we’ve integrated our platform with Rapid7 InsightVM to ensure that our customers have full visibility into their security posture, including endpoints, and that they know how to prioritize remediation.