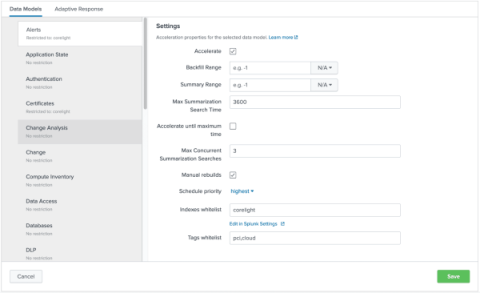
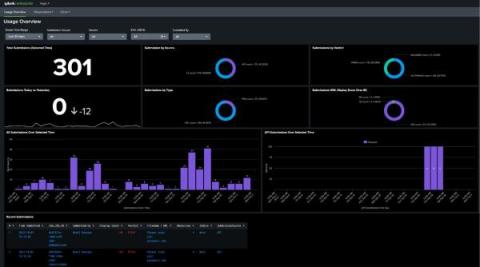
Enhance your search experience within Splunk by using the Corelight App
The Corelight App for Splunk provides the foundation for organizations to boost SOC effectiveness and productivity by using Corelight data in Splunk. In this blog, I’ll walk through how the Corelight App leverages Splunk’s Common Information Model (CIM) to enhance users' search experience when they are using Corelight data.