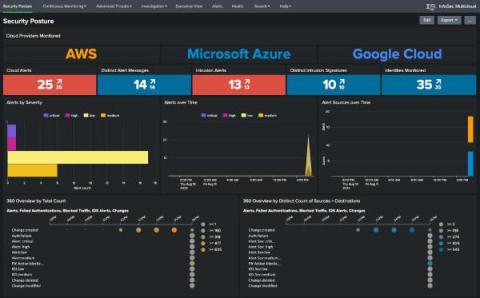
Falcon LogScale Live Dashboards: Demo Drill Down
Monitoring security events in real-time empowers you to find stealthy threats and spot attack trends early. See how Falcon LogScale’s live dashboards provide a flexible, intuitive way to visualize your security data. You'll learn how to build a MITRE ATT&CK dashboard that automatically updates with live data.