Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Coffee Talk with SURGe: 2023-10-31 SEC SolarWinds Complaint, Biden's Executive Order on AI
More Than Just a RAT: Unveiling NjRAT's MBR Wiping Capabilities
SOARing High for M-21-31
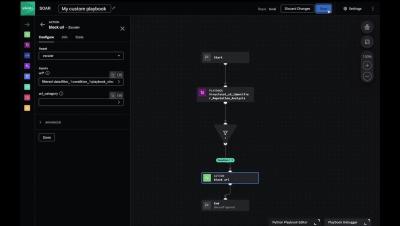
Splunk SOAR Playbooks - Dynamic Identifier Reputation Analysis (Part 2)
Keeping Perspective Amongst the Sometimes Tumultuous Cybersecurity Environment
A SOC analyst role is equal parts fulfilling and overwhelming. On one hand, the landscape is dynamic and the work is critical to protecting organizations. On the other, the weight of continual responsibility can lead to stress, anxiety, and cybersecurity burnout. Understanding the importance of your mental health is crucial to maintaining productivity and preventing cybersecurity burnout.
User and Entity Behavior Analytics (UEBA) For Enterprise Security
How to Spot a Next-Gen SIEM Imposter
Staying ahead of the cybersecurity curve can feel like running a marathon uphill, and the right SIEM is key to leveling the playing field. Smarter SIEM solutions have emerged from the cloud to address the changing demands of today’s security operations. Unlike legacy SIEMs, which were designed for on-premises deployments and have limited scalability, more innovative next-gen solutions offer cloud-native SaaS models that provide greater flexibility and scalability.
How the MITRE ATT&CK Framework Helps CISOs Communicate Risk to Stakeholders
Picture this: Your CEO comes into your office and asks, “What’s our security posture, and where’s our greatest area of risk? I’m particularly worried about this new emerging threat group. What defenses or detections do we have around that?” You: “…” Enter the MITRE ATT&CK® framework and Devo’s MITRE ATT&CK Adviser app—built to help you tell the business where your risks are and what it would take to address them.
Does Your SIEM Empower Your SOC?
The right SIEM can make or break your SOC. While there are a lot of security solutions and platforms for you to choose from, ask yourself–how will they make life in your SOC better than before? If you make the right choice, you’ll empower your SOC to work more efficiently, more effectively, and more proactively. As you do your research and consider which SIEM is right for you, make sure it checks these boxes. Your analysts will thank you.