Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
CSPM - Least privilege principle in practice
Cloud Security Posture Management (CSPM) aims to automate the identification and remediation of risks across your entire cloud infrastructure. A core requirement of the CSPM framework is the need to enforce a principle of least privilege. There are certain overlaps with Cloud Infrastructure Entitlement Management (CIEM) solutions. CIEM is a newer categorization that came after CSPM.
Securing a Kubernetes Cluster | 5 Tips
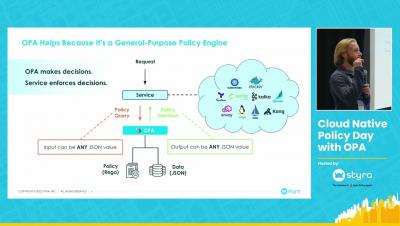
Policy as Code with Azure API Management (APIM) and OPA
A common use case for Open Policy Agent (OPA) is to decouple authorization from the application. This enables policies and decisions to be managed centrally and lifecycled independently to the application. For application use cases, OPA can be integrated at the API Gateway, Service Mesh or Microservices layer or any combination of these.
Meeting PCI DSS Compliance with Styra DAS + Kubernetes
DevOps and platform teams are more strained than ever, and as a result, need better tools than ever. These teams are required to develop, provide access to, and secure a number of resources — while remaining good stewards to application developers. Beyond that, they are often tasked with overseeing their organization’s shift to the cloud. And as that shift takes place, DevOps teams will need to shift their compliance standards to the cloud.
Snowflake: SansShell: A Non-interactive Daemon for Host Management
Styra: Authorization: The Data Gravity Problem
Setting up SSL/TLS for Kubernetes Ingress
Today, web and mobile applications and API-based microservice endpoints are becoming the default. These applications are reachable through the HTTP web protocol. The encryption provided by a Secured Socket Layer or Transport Layer Security (SSL/TLS) is a must to secure the communication between client and server and across API back-ends. SSL/TLS are certificate-based encryption mechanisms. SSL has been the standard for over 20 years.
Microservices Security: Fundamentals and Best Practices
The many benefits of microservices architecture, such as improved scalability and agility, explain why organizations are migrating from the traditional monolithic architecture. However, these benefits come at the cost of increased complexity, especially regarding security. According to an O’Reilly survey, 56% of respondents considered increased complexity the greatest challenge in developing microservices.