Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
Comparing GuardDuty & Falco on EKS
Security in cloud providers like AWS is usually the highest priority. With EKS, unlike bring-your-own vanilla Kubernetes instances, you benefit from a data center and network architecture that is built to meet the requirements of the most security-sensitive organizations. To achieve this, one of the best ways is to use all the security layers we are capable of having. In this case, we will explain how to use GuardDuty and Falco to speed up threat detection.
Discovered new BYOF technique to cryptomining with PRoot
The Sysdig Threat Research Team (TRT) recently discovered threat actors leveraging an open source tool called PRoot to expand the scope of their operations to multiple Linux distributions and simplify their necessary efforts. Typically, the scope of an attack is limited by the varying configurations of each Linux distribution. Enter PRoot, an open source tool that provides an attacker with a consistent operational environment across different Linux distributions, such as Ubuntu, Fedora, and Alpine.
8 Benefits of Externalized Authorization Management (EAM)
The evolution of application design and cloud-native technologies means that developers can no longer rely on traditional authentication and authorization methods to be effective. While new standards for authentication already exist and are easily implemented, authorization remains a challenge, especially in a fast-paced, dynamic cloud environment. One method of solving this issue is to externalize authorization, allowing policy management to be decoupled from the application itself.
What Is Fine-Grained Access Control?
A data and security breach often leads to fines and the loss of customer trust for organizations. An IBM report estimates that a data breach on average costs $4.35 million in 2022, a 2.6% increase from the previous year. The increased concern with data and security breaches — along with the need to address more complicated use cases — reinforces the call for more granular methods of access control.
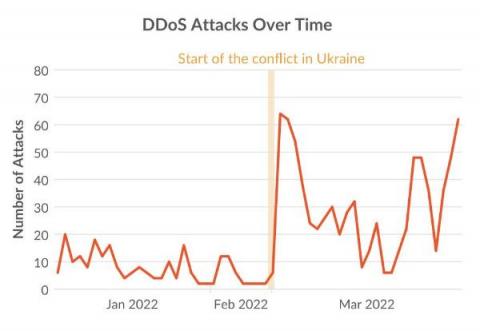
How the Russia-Ukraine conflict changed cyber attacks: More attacks, More DDoS
The conflict between Russia and Ukraine includes a cyberwarfare component with government-supported threat actors and civilian hacktivists taking sides. The goals of disrupting IT infrastructure and utilities have led to a 4-fold increase in DDoS attacks between 4Q21 and 1Q22. Over 150,000 volunteers have joined anti-Russian DDoS campaigns using container images from Docker Hub.
Extortion in Cloud Storage
Extortion can simply be defined as “the practice of obtaining benefit through coercion.“ Data and cloud extortion schemes occur when precious data and/or access is stolen by an attacker that promises to restore it through payment or other demands. In this article, we’ll cover some common or uncommon extortion schemes, and highlight ways to detect and avoid falling prey to demands.
Kubernetes Version 1.26: Everything You Should Know
2022 Kubernetes Vulnerabilities - Main Takeaways
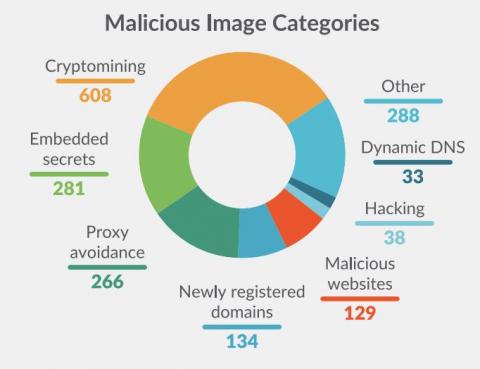
Analysis on Docker Hub malicious images: Attacks through public container images
Supply Chain attacks are not new, but this past year they received much more attention due to high profile vulnerabilities in popular dependencies. Generally, the focus has been on the dependency attack vector. This is when source code of a dependency or product is modified by a malicious actor in order to compromise anyone who uses it in their own software.