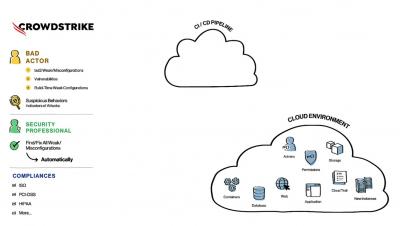
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
ARMO adds CIS EKS benchmark
Understanding Kubernetes Architecture and Components
Kubernetes secrets management: 3 approaches and 9 best practices
Secrets, such as usernames, passwords, API tokens, and TLS certificates, contain confidential data that can be used to authenticate and authorize users, groups, or entities. As the name implies, secrets are not meant to be known or seen by others. So how do we keep them safe? The key to keeping secrets safe lies within how you manage them.
Why the Wiz/SentinelOne Partnership Validates the Sysdig Approach
With today’s announcement of the Wiz/SentinelOne partnership and other recent launches, like Orca/ThreatOptix, we are seeing cloud security players publicly validate that they can no longer compete without a compelling runtime security solution. Agentless technology enabled young companies to solve the low-hanging fruit problem of periodic cloud security assessment.
Learn OPA for Kubernetes Admission Control with Styra Academy
As enterprises build and run cloud-native applications on Kubernetes, platform engineering teams are responsible for empowering dozens, hundreds or even thousands of developers to rapidly configure the right infrastructure resources to run mission-critical applications. At the same time, today’s complex threat landscape and strict regulatory environment make it increasingly difficult for developers to configure secure and compliant infrastructure.
MITRE ATT&CK and D3FEND for Cloud and Containers
MITRE ATT&CK and MITRE D3FEND are both frameworks developed by the non-profit organization MITRE, but they serve different purposes. If you are new to the MITRE ATT&CK framework and would like to brush up on some of the concepts first, we created a Learn Cloud Native article to help you on your journey. If you want to go further, here’s how Falco’s Cloudtrail rules align with MITRE ATT&CK.
Testing the actual security of the most insecure Docker application
Our previous research on CVE exploitability in the top DockerHub images discovered that 78% of the reported CVEs were actually not exploitable. This time, the JFrog Security Research team used JFrog Xray’s Contextual Analysis feature, automatically analyzing the applicability of reported CVEs, to scan OWASP WebGoat – a deliberately insecure application. The results identified that out of 60 CVEs reported with a Critical CVSS score, only 10 are actually applicable.
SCARLETEEL: Operation leveraging Terraform, Kubernetes, and AWS for data theft
The Sysdig Threat Research Team recently discovered a sophisticated cloud operation in a customer environment, dubbed SCARLETEEL, that resulted in stolen proprietary data. The attacker exploited a containerized workload and then leveraged it to perform privilege escalation into an AWS account in order to steal proprietary software and credentials. They also attempted to pivot using a Terraform state file to other connected AWS accounts to spread their reach throughout the organization.
3 Ways To Address Your Kubernetes Data Protection Challenges
Kubernetes is an open-source container orchestration tool originally developed by Google for managing microservices or containerized applications across a distributed cluster of nodes. It is widely thought that “Kubernetes is key” to cloud-native application strategies. Kubernetes (K8s) runs over several nodes, and the collection of nodes is called a cluster. K8s clusters allow application developers to orchestrate and monitor containers across multiple physical, virtual, or cloud servers.