Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
CloudCasa Security Overview
As a developer of copy data management and data protection products for 20+ years, Catalogic Software has considerable experience in securing and protecting our customers’ data. For our new CloudCasa backup service for Kubernetes and cloud native databases, security is built into every step of the service using a modern DevSecOps approach. In addition, we are adding new capabilities to meet specific enterprise security and data custodian and governance requirements.
Detecting MITRE ATT&CK: Defense evasion techniques with Falco
The defense evasion category inside MITRE ATT&CK covers several techniques an attacker can use to avoid getting caught. Familiarizing yourself with these techniques will help secure your infrastructure. MITRE ATT&CK is a comprehensive knowledge base that analyzes all of the tactics, techniques, and procedures (TTPs) that advanced threat actors could possibly use in their attacks. Rather than a compliance standard, it is a framework that serves as a foundation for threat models and methodologies.
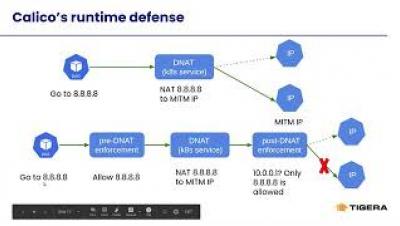
Calico Enterprise Multi Cluster Management - Federated Identity and Services
Snyk and Rapid7 strengthen partnership to provide a holistic risk assessment solution for container applications
Modern organizations are working hard to differentiate their products and services by creating innovative solutions that their customers can leverage at home and on-the-go, forcing them to consider new, more agile approaches to application development that empower their development teams to accelerate time-to-market, and launch new solutions as quickly as possible.
TeamTNT delivers malware with new detection evasion tool
AT&T Alien Labs™ has identified a new tool from the TeamTNT adversary group, which has been previously observed targeting exposed Docker infrastructure for cryptocurrency mining purposes and credential theft. The group is using a new detection evasion tool, copied from open source repositories. The purpose of this blog is to share new technical intelligence and provide detection and analysis options for defenders.
Integrating identity: OAuth2 and OpenID Connect in Open Policy Agent
In order to make policy decisions we commonly need to know the identity of the caller. Traditionally this has often been done by providing a user or client identifier along with the request, and using that identifier to look up further information like user details or permissions from a remote data source. While this model works fairly well for many applications, it scales poorly in distributed systems such as microservice environments.
Docker for Node.js developers: 5 things you need to know not to fail your security
Docker is totalling up to over 50 billion downloads of container images. With millions of applications available on Docker Hub, container-based applications are popular and make an easy way to consume and publish applications. That being said, the naive way of building your own Docker Node.js web applications may come with many security risks. So, how do we make security an essential part of Docker for Node.js developers?
Microservices, Containers and Kubernetes in 10 minutes
What is a microservice? Should you be using microservices? How are microservices related to containers and Kubernetes? If these things keep coming up in your day-to-day and you need an overview in 10 minutes, this blog post is for you. Fundamentally, a microservice is just a computer program which runs on a server or a virtual computing instance and responds to network requests.