Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
Running commands securely in containers with Amazon ECS Exec and Sysdig
Today, AWS announced the general availability of Amazon ECS Exec, a powerful feature to allow developers to run commands inside their ECS containers. Amazon Elastic Container Service (ECS) is a fully managed container orchestration service by Amazon Web Services. ECS allows you to organize and operate container resources on the AWS cloud, and allows you to mix Amazon EC2 and AWS Fargate workloads for high scalability.
Detecting and mitigating Apache Unomi's CVE-2020-13942 - Remote Code Execution (RCE)
CVE-2020-13942 is a critical vulnerability that affects the Apache open source application Unomi, and allows a remote attacker to execute arbitrary code. In the versions prior to 1.5.1, Apache Unomi allowed remote attackers to send malicious requests with MVEL and OGNL expressions that could contain arbitrary code, resulting in Remote Code Execution (RCE) with the privileges of the Unomi application.
Linting Rego with... Rego!
One of my absolute favorite aspects of Open Policy Agent (OPA) is the general purpose nature of the tool. While commonly seen in deployments for Kubernetes admission control or application authorization, the large OPA ecosystem includes integrations with anything from databases, and operating systems to test frameworks and REST clients for most common languages.
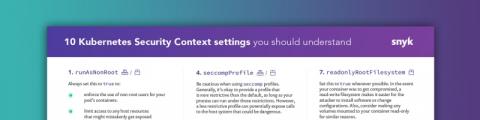
10 Kubernetes Security Context settings you should understand
Securely running workloads in Kubernetes can be difficult. Many different settings impact security throughout the Kubernetes API, requiring significant knowledge to implement correctly. One of the most powerful tools Kubernetes provides in this area are the securityContext settings that every Pod and Container manifest can leverage. In this cheatsheet, we will take a look at the various securityContext settings, explore what they mean and how you should use them.
Retailers Need Unified Cloud Policy in Today's Hyper-Agile Era
In this pandemic-defined era of rapid retail transformation, the digital shopping experience has become tantamount to the success of the business. As a result, retailers have redoubled their efforts to improve digital applications and services.
Breaking Containers to Improve Security: Docker and Snyk
Detecting MITRE ATT&CK: Privilege escalation with Falco
The privilege escalation category inside MITRE ATT&CK covers quite a few techniques an adversary can use to escalate privileges inside a system. Familiarizing yourself with these techniques will help secure your infrastructure. MITRE ATT&CK is a comprehensive knowledge base that analyzes all of the tactics, techniques, and procedures (TTPs) that advanced threat actors could possibly use in their attacks.
Using OPA with GitOps to speed cloud-native development
Devops teams are flocking to GitOps strategies to accelerate development time frames and eliminate cloud misconfigurations. They should adopt a similar ‘as-code’ approach to policy. One risk in deploying fleets of powerful and flexible clusters on constantly changing infrastructure like Kubernetes is that mistakes happen. Even minute manual errors that slip past review can have substantial impacts on the health and security of your clusters.
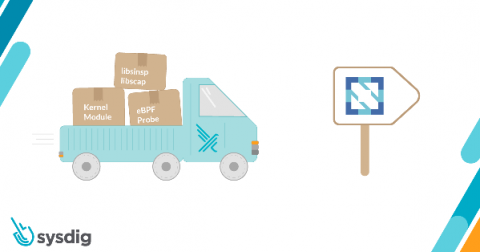
Sysdig contributes Falco's kernel module, eBPF probe, and libraries to the CNCF
Today, I’m excited to announce the contribution of the sysdig kernel module, eBPF probe, and libraries to the Cloud Native Computing Foundation. The source code of these components will move into the Falco organization and be hosted in the falcosecurity github repository. These components are at the base of Falco, the CNCF tool for runtime security and de facto standard for threat detection in the cloud.