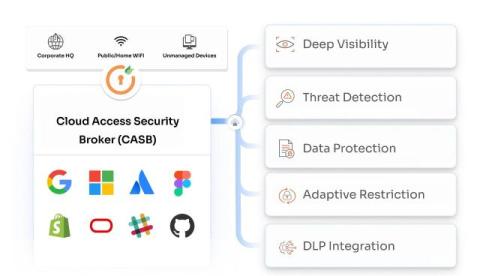
Beyond Analyst Reports: KnowBe4's Undeniable Leadership in Human Risk Management
Analyst reports aim to provide market insights. But when it comes to Human Risk Management (HRM), we’ve noticed that they often fall short of capturing the full picture. You already know that we are the undisputed leader in the essential areas that have been standard features in the security awareness market for years. Those capabilities are why we’ve become the largest vendor in the space. But for years now we have exceeded just those standard features.