Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Product Release
One Identity Manager version 9.2 has been released GA
Identity Manager governs and secures your organization’s data and users, meets uptime requirements, reduces risk and satisfies compliance by giving users access to data and applications they need – and only what they need – whether on-premises, hybrid or in the cloud. Now, identity security can be driven by business needs, not by IT capabilities. With Identity Manager, you can unify security policies and satisfy governance needs — today and long into the future.
Unveiling public leak checks for hardcoded secrets in the GitGuardian Platform
GitGuardian can now help you check if your (already) hardcoded secrets have not also leaked publicly in code, issues and gists of projects located outside your GitHub organizations.
CrowdStrike Brings AI-Powered Cybersecurity to Small and Medium-Sized Businesses
Cyber risks for small and medium-sized businesses (SMBs) have never been higher. SMBs face a barrage of attacks, including ransomware, malware and variations of phishing/vishing. This is one reason why the Cybersecurity and Infrastructure Security Agency (CISA) states “thousands of SMBs have been harmed by ransomware attacks, with small businesses three times more likely to be targeted by cybercriminals than larger companies.”
Rubrik Unveils Rapid Cyber Recovery for Large Enterprises Using Microsoft 365 Backup Storage
Every day more than 2 billion documents and emails are added to Microsoft 365, making this critical data a priority target for ransomware and other cyber attacks. After all, 61% of attacks affect SaaS applications, the most targeted platform / environment. This data can also often be unstructured, and rapidly processing and managing the content at enterprise scale is critical when it comes to both applying protection and performing restores.
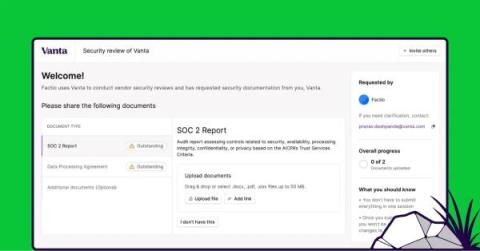
Introducing Private Links: A faster, easier way to gather vendor security information
When it comes to conducting vendor security reviews, the two most time-consuming tasks are gathering the relevant information from your vendor and analyzing it thoroughly. Last month, we announced AI-powered security document analysis to drastically simplify the process of extracting insights from SOC 2 reports, DPAs, and other sources that document a vendor’s security posture.
CyberArk Identity 23.11 Release
CyberArk MFA now supports authentication with phishing-resistant passkeys and qualifies for the highest NIST Authenticator Assurance Level (AAL3). Based on FIDO2 standards, passkeys replace passwords and provide faster, easier and more secure sign-ins to websites and apps across user devices. With this release, end users can authenticate using passkeys to access their applications and resources.
Welcome to the Future of SD-WAN - The Next Gen SASE Branch
It’s been a long journey toward securing and optimizing the enterprise branch, from the days of rigid MPLS networks to the agile era of SD-WAN. Now comes the next stage of that journey: Secure access service edge (SASE), which, when architected correctly, converges the most important network and security capabilities into a single cloud-delivered service. Before we talk about how, though, let’s examine why SASE’s moment is now.
What's new in Elastic Security 8.11: Piped queries, AI assistance, and cloud and user data
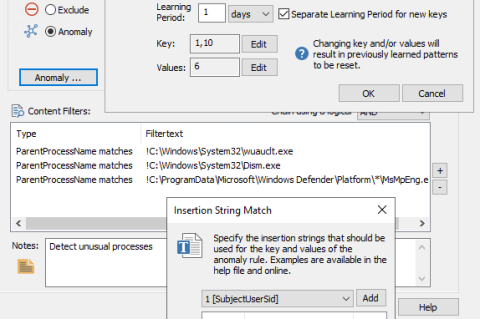
EventSentry v5.1: Anomaly Detection / Permission Inventory / Training Courses & More!
We’re extremely excited to announce the availability of the EventSentry v5.1, which will detect threats and suspicious behavior more effectively – while also providing users with additional reports and dashboards for CMMC and TISAX compliance. The usability of EventSentry was also improved across the board, making it easier to use, manage and maintain EventSentry on a day-by-day basis. We also released 60+ training videos to help you get started and take EventSentry to the next level.