Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
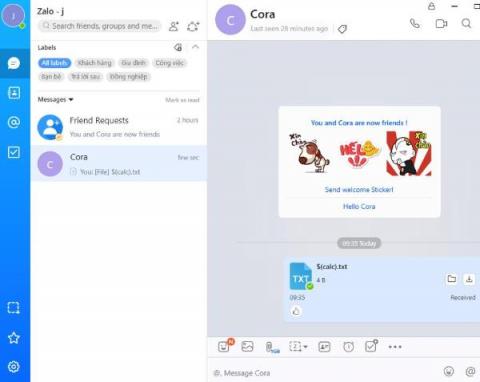
Remote Code Execution in a Popular Chat App: Easy as Sending a File
Zalo is a chat application on the rise and exceedingly popular in South-East Asia with a user base of over 100 million. In a number of countries, including Vietnam and Myanmar, the application rivals WhatsApp and Facebook Messenger as the most popular chat application. Zalo’s functionality continues to expand with Zalo Pay and Zalo Shop emerging among many new features on the burgeoning super app.
Introducing Datadog Compliance Monitoring
Governance, risk, and compliance (GRC) are major inhibitors for organizations moving to the cloud—and for good reason. Cloud environments are complex, and even a single misconfigured security group can result in a serious data breach. In fact, asset misconfigurations were the leading cause of cloud security breaches in 2019. This puts a lot of pressure on developer and operations teams to properly secure their services and maintain regulatory compliance.
Nearly 50 Percent of Organizations Knowingly Push Vulnerable Software, According to New Research from ESG and Veracode
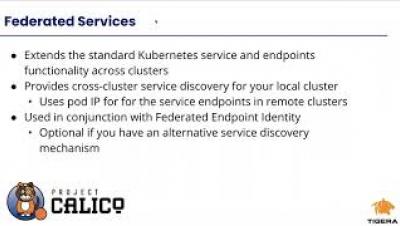
Calico Enterprise Multi Cluster Management - Federated Identity and Services
New ESG Survey Report: Modern Application Development Security
As organizations continue to adopt DevSecOps, a methodology that shifts security measures to the beginning of the software development lifecycle (SDLC), roles and processes are evolving. Developers are expected to take on increased security measures – such as application security (AppSec) scans, flaw remediation, and secure coding – and security professionals are expected to take on more of a security oversight role.
Elastic Security: How to Plan and Execute a Hunt
New Agent Tesla Variants Capable of Stealing Data from VPNs, Browsers
Some new variants of the Agent Tesla infostealer family are capable of stealing data from multiple VPN clients and web browsers. SentinelOne observed that attackers continue to deploy Agent Tesla across various stages of their operations, as this malware enables criminals with even low levels of technical expertise to manipulate and manage their victims’ infected devices.
Cyber Security Approach for SMEs
I was asked the following recently in an interview for the Irish tech online magazine 'Silicon Republic’; How can companies make sure they are spending on cyber security in the right way? I thought it was a great question. In the article, I answered in general, however it got me thinking on elaborating on this with the particular focus for SMEs, who especially at this time are feeling the pinch of the revenues lost by COVID-19.
Identify API Incidents with Built-in Anomaly Rules
One of Bearer's super powers is anomaly detection. Anomalies are unexpected issues that happen when making an API call. These could be high error rates, unexpected response codes, latency spikes, and more. By monitoring APIs with anomaly detection, we can identify problems with an API or within your application. Anomaly detection makes debugging easier and can help you identify API performance issues that affect your end users.