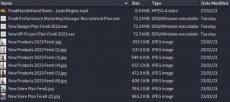
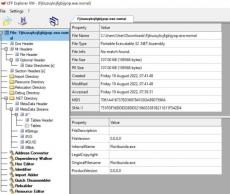
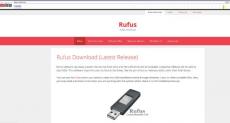
The high profile MGM Resorts hack by ransomware group ALPHV/BlackCat has served as a wake up call to the hospitality industry, demonstrating that the industry is a lucrative target for cybercriminals. The hack was hugely impactful to MGM making for sensational headlines in mainstream media, however what struck security experts were the social engineering methods used by the threat actors and how effective they were in bypassing security controls and technologies.
|
By Aaron Hau
In a recent social-engineering attack targeting the hospitality sector observed by the ThreatSpike team, there appears to be a change in the tactics employed by the threat actor. The hospitality sector, where top-notch customer-service is expected, customer-facing employees are often lucrative targets for phishing, as detailed in our previous blog post.
|
By Aaron Hau
Humans are the weakest link in cybersecurity, and it is inaccurate to say that IT administrators, who often have access to sensitive data and systems, are invulnerable. In this blog post, we demonstrate how a Red Team Operator achieved full Active Directory domain compromise as a result of an IT Administrators’ poor cyber hygiene.
|
By Jacob Andrews
In recent years, phishing attacks have become increasingly sophisticated and are now being conducted through various messaging platforms such as Telegram. Telegram is a popular messaging app that allows users to send messages, photos, videos, and other files over the internet. It also provides APIs that allow developers to create custom bots and applications. Unfortunately, these same APIs can be used by malicious actors to exfiltrate credentials successfully phished from attacks.
Featured Post
Despite the growing awareness of the necessity for more advanced cyber security, firms are still falling foul of attacks which are undetected when they arrive and can stay for years. Adam Blake, CEO and Founder of ThreatSpike discusses the reasons why businesses are missing the mark and how they can keep one step ahead of cyber-attacks.
|
By Chandler Geary
High-profile ransomware attacks against large businesses and governments have become increasingly popular. They typically occupy news headlines on a monthly basis. As of writing, the most recent, high-profile attack was launched against Porsche, South Africa, where IT systems and some backups were impacted by ransomware from an unknown attacker. The gangs that perpetrate these attacks typically have carefully-crafted, large public personas and engage in significant posturing.
Since late December 2022, the ThreatSpike team has noticed a significant rise in highly targeted phishing campaigns aimed at the hospitality sector, which distribute infostealer malware. The threat actors (TAs) are primarily targeting front desk and reception staff, as they are responsible for handling customer queries via a generic email that can easily be found on the company website.
|
By Gagandeep Mehta
Redline infostealer gathers information and steals high value data from an infected machine. The Redline infostealer is considered one of the most dangerous malware currently being used in the wild and has been used in countless trojanized software, applications, games and cracked software. In addition to data exfiltration, Redline also has the capability to connect to a command and control (C2) server to download, upload files as well as perform remote commands.
|
By ThreatSpike
Industry-first fixed price managed offensive security service aims to close the cybersecurity gap, strengthen customers' cyber defence posture, and reduce risk.
|
By Gagandeep Mehta
This blog post will provide an analysis of the malicious Redline Infostealer payloads which have been taken from a real life malware incident, responded to and triaged by the ThreatSpike SOC team. This analysis will be broken down to demonstrate, describe and explain the various stages of the attack chain.
- November 2023 (1)
- June 2023 (1)
- April 2023 (1)
- March 2023 (3)
- February 2023 (2)
- January 2023 (2)
- February 2021 (1)
- January 2021 (5)
- August 2020 (1)
- May 2020 (1)
- January 2020 (1)
ThreatSpike Labs provides the first end-to-end fully managed security service for companies of all sizes. We monitor networks for a broad range of security issues, tailoring our monitoring for the specific industry and requirements of each customer.
ThreatSpike's software defined security platform takes only a few hours to install after which time all activity on the network is monitored by a team of highly trained analysts and penetration testers. Companies are alerted in real time to any active threats, as well as weaknesses that could be used by attackers at a later time.
What can ThreatSpike detect?
- Hacking: We monitor for hacking including reconnaissance, network and application exploits as well as lateral movement.
- Malware: We use methods including machine learning to detect malicious executables, command and control activity as well as network propagation.
- Vulnerabilities: We monitor for weaknesses in technology systems and business processes that may be used to steal data and commit fraud.
- Insider Threats: We monitor logins, authorisation changes, access reach, electronic communications and data transfers to detect insider threats.
One Platform. One Partner. Complete Security.