The Dark Side of Online Bookings: Infostealers and Phishing in the Hospitality Industry
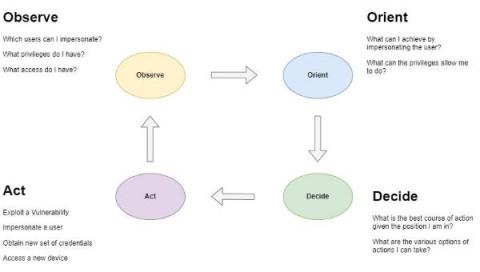
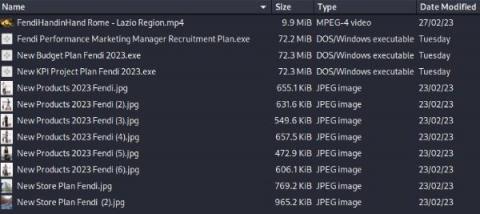
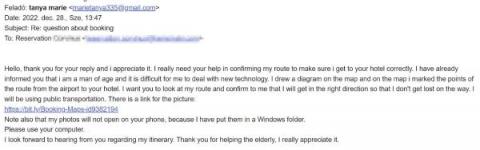
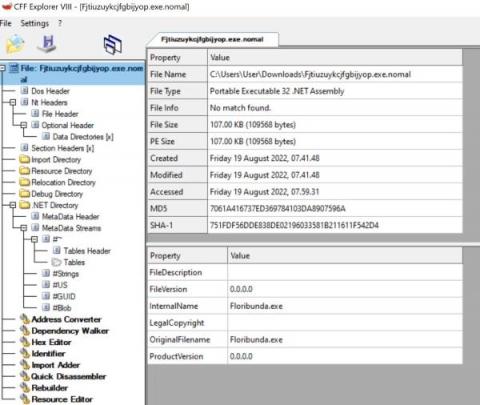
The high profile MGM Resorts hack by ransomware group ALPHV/BlackCat has served as a wake up call to the hospitality industry, demonstrating that the industry is a lucrative target for cybercriminals. The hack was hugely impactful to MGM making for sensational headlines in mainstream media, however what struck security experts were the social engineering methods used by the threat actors and how effective they were in bypassing security controls and technologies.