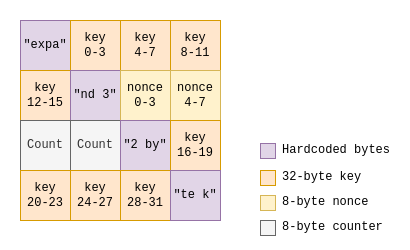
Critical triggers to reassess your SIEM: when and why to evaluate
You wouldn’t drive a car that hasn’t been serviced in a decade. So why are you still trusting a legacy SIEM solution? The world of cybersecurity is in a constant state of flux, and your security information and event management (SIEM) needs to keep up. If you’re not regularly reassessing it, you might as well roll out the red carpet for hackers. Let’s discuss when and why you should seriously consider giving your SIEM a much-needed check-up.