From Risk to Fix in a Single Click: How CultureAI Are Redefining Nudges in Cyber Security
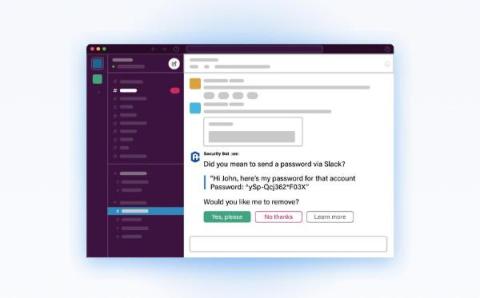
The term 'nudge' has become a buzzword in cyber security over recent years, often being mistakenly equated with 'notifications'. CultureAI aims to shift this perception by leveraging Nudge Theory principles to implement actionable Nudges.